Beauty and The Breach: Leaked Credentials in Context
Michael Marriott, Digital Shadows security expert
Our most recent research paper looks at credential compromise, finding more than 5 million leaked credentials online for the world’s biggest 1,000 organizations. Of course, not all breached data is of equal value and, in order to better understand the desirability of the data and the severity of the breach, it’s important to consider six factors.
- Recoverable passwords – data dumps with recoverable passwords, such as the LinkedIn breach of 2012, are more useful than those without
- Data sensitivity – highly sensitive or damaging data may be used by a threat actor in blackmail or extortion attempts, such as the Ashley Madison breach of 2015, or, in the case of health records, for identity theft
- Freshness – as a data set get older its usefulness declines as those contained with the data set either abandon accounts or change passwords
- Transferability – some data set are just more relevant to an individual than others, especially datasets containing reusable information for other accounts (such as addresses, secret questions and credit card details)
- Size – how accurately does the data represent the target user group? 50%? 70%? Critically, how accurately does the data represent the target user group in relation to the desired outcome of the threat actor?
- Public or private source – the more ‘secretive’ the data, the more useful it would be for a threat actor. Also, if a dataset has been made public, the affected organization is highly likely to revoke exposed passwords
The six factors outlined above can be used both to assess the severity of a breach as well as to make a comparison between breaches.
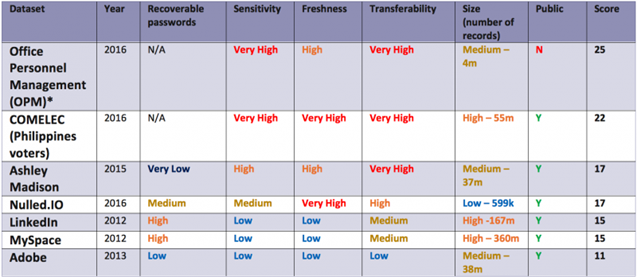
Our research paper takes over 30,000 instances of claimed leaked credentials to understand how the world’s 1,000 biggest organizations are impacted. For this post, we have taken seven historical breaches of varying size and content to see how they measured up against these factors of desirability and against each other. Although the Office of Personnel Management (OPM) breach is not publically available, it has been included for comparative purposes.
*Digital Shadows do not have access to this dataset
Table 1: Historical breaches measured against factors of desirability
Based on the above matrix the following conclusions can made about what makes a dataset attractive:
- The six-point scale is useful in its own right, but it gives greater insight when it is used to compare other data breaches. The comparative exercise also validates the overall methodology
- The most attractive dataset included within the above matrix is the one that is not public (OPM). While one factor does not make a trend, this strongly suggests that closed source data sets have a far greater impact than more openly available data sets
- Not all the fields are equally weighted – it would appear that size does not seem to matter as much in comparison to other factors such as sensitivity, transferability, and whether or not the data is public
- Passwords are not the be all and end all – simply being present within a highly sensitive breach such as Ashley Madison can be far more damaging
- Breaches scoring highly on Sensitivity, Freshness and Transferability ranked the highest. The sensitivity of dataset can be used to facilitate extortion, while its freshness and transferability would be invaluable for an actor attempting to gain access to other accounts, or to extensively profile an individual for reconnaissance purposes. The different ways in which threat actors can use historic breached data will be explored in greater detail in our next blog.
Shown below is a full explanation of the reasoning behind the grading within the matrix, readers are invited to apply the matrix themselves.
Severity Scoring: Very High=5, High=4, Medium=3, Low=2, Very Low=1, Non-public=5, Public=0, N/A=3
Table 2: Severity matrix for factors of desirability
Download a copy of Digital Shadow research paper, “Compromised Credentials – Learn From the Exposure of the World’s 1,000 Biggest Companies”, to understand the impact of leaked credentials on organizations.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!