Fake Fortnite for Android links found on YouTube
The extremely popular video game Fortnite is coming to Android sometime this summer, and the fan base is going wild. Not surprisingly, mobile malware developers are taking advantage. Already, there are several videos on YouTube with links claiming to be versions of Fortnite for Android, despite the fact the game has yet to be released on this platform.
Swati Khandelwal of The Hacker News highlights the emerging threat in her article, Epic Games Fortnite for Android–APK Downloads Leads to Malware. Taking it a step further, I grabbed some of these malicious apps and took them for a spin.
The source of infection
The apps are not located on the Google Play Store. Instead, people have found them by searching “How to install Fortnite on Android” or “Fortnite for Android” in Google, or stumbling across links in YouTube ads. From there, the apps can be downloaded.
My findings for the so-called Fortnite for Android app are that it’s a simple program that comes in two different package names (so far):
com.anizz14
com.anizz14.fortnite
Simple, but malicious nonetheless
To make the app look legit, it starts with a realistic-looking icon. As a matter of fact, it’s so realistic that some may recognize it from the Apple iOS version. By stealing the icon directly from Apple, how could it not look real?

When opening the app, it displays the Epic Games logo to further trick users.

Next, once again stealing from iOS, a loading screen appears.

iOS stolen loading screen
After the loading screen, it starts playing the Fortnite intro song and opens a screen that displays “New Updates,” the first indication something might be up.
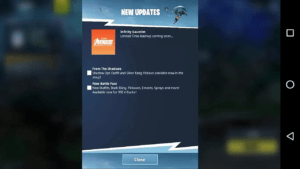
By just clicking on the screen, it moves onto a different screen that makes more sense. It states that it’s “Logging In…” and looks very authentic (as well as very stolen).

The next screen is where things go sideways. It requires a Mobile Verification.
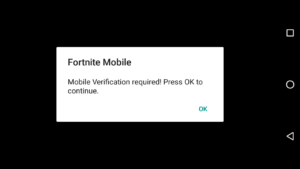
Click “OK” and the app redirects to a website via your default browser. There, it claims to be for the purpose of verifying “You’r Not A BOT” (bad grammar and all) in order to proceed to Fortnite. To “verify,” the user must complete a task, which involves downloading another “free” app.

Click on a link and a pop-up promising “Unlock Instructions” appears.
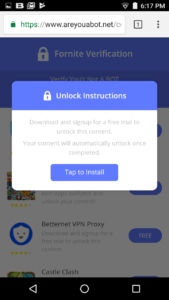
Press “Tap to Install” and it redirects you to Google Play—that’s right, a bit of silver lining. The redirect is at least to a legit, safe Google Play version of an app.

The bad news is that no matter how many apps you download, the game never unlocks—because it never existed within the malicious app in first place.
Yep, I know this game
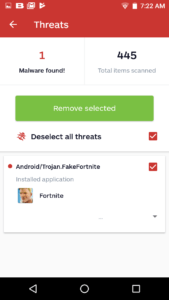
The scheme goes like this: Get a couple of over-excited people salivating for a chance to play Fortnite on Android, and get paid. The more downloads that come from the website shown above, the more money the malware developers can make. With the app being so simplistic, the amount of development effort is pretty low for the amount that could be potentially gained. Hopefully, we can help stop the revenue stream by detecting this one as Android/Trojan.FakeFortnite.
Patience is a virtue
Every time there is craze around a new video game release, consequently we see malware authors jumping into the game. Often, it’s an attack against our good senses. They capitalize on that little itch that screams “I want it now!” We suggest listening to that other inner voice that warns, “This seems too good to be true.” Our advice: be patient. If you wait for the official release by Epic Games in the Google Play Store this summer, you won’t have the spend the ensuing months cleaning malware off your Android. Stay safe out there!






