SWOTTING UP ON EXPLOIT KIT INFECTION VECTORS
Exploit kit users need to drive web traffic to their landing pages. Without traffic, they can’t exploit vulnerable web users and serve malicious software (the objective of an exploit kit almost all of the time). The more visitors they get, the more likelihood there is of a successful exploitation and a successful infection. For exploit kit users, that means using the best routes to infection. For us, that means understanding why they are used. We can look at the routes to exploit kit infection from a user’s perspective to teach us about attacker techniques. This can allow us to perceive, understand and possibly project the likely activity of these techniques in the near future.
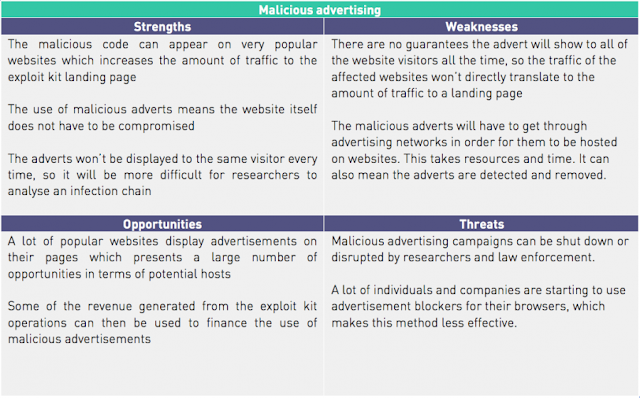
As it stands, there are three main distribution methods; malicious advertisements, compromised websites injected with code, and spam emails. All of these rely on the presence of malicious code that can redirect a web page visitor to an exploit kit landing page. Taking a threat actor’s perspective, I’ve outlined the strengths, weaknesses, opportunities and threats below.
Table 1 – Red team SWOT analysis of Malvertising
Table 2 Red team SWOT analysis of using compromised sites
When we consider the strengths, weaknesses, opportunities and threats for an exploit kit operator looking to drive traffic to their landing pages, we can rank them in the following order of effectiveness.
- Malicious adverts
- Compromised websites
- Spam emails
While all of these methods are considered viable by exploit kit operators, the analyses above show factors that are likely to contribute to the extent of their use. The benefits of using malicious adverts are likely to contribute to the extent of this method’s use, while the weaknesses of the spam method is a likely reason for it being less widespread. While this is true, spam emails were once a major part of BlackHole exploit kit activity in 2013.
For me, the largest factors associated with the use of malicious advertisements was the fact malvertising can generate a large amount of traffic to an exploit kit landing page, simply because those adverts can appear on popular websites.
While the use of compromised websites presents advantages in relation to the malicious code always being presented to visitors, depending on parameters set by the threat actors, the compromise is reliant on the security practices of the website administrators in the first instance. Social engineering attempts, while useful in driving traffic to compromised websites, are likely to arouse more suspicion and require additional effort beyond an initial website compromise. Given these factors, we assessed it to be likely that malicious advertising would remain the most prevalent form of exploit kit distribution in future, assuming that no mitigation methods were implemented by advertising networks or websites hosting adverts that would disrupt these campaigns.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!