This year, the North Atlantic Treaty Organization (NATO) members and the White House are the newest targets of the long-running APT campaign Operation Pawn Storm, along with an introduction of new infrastructure.
Latest intelligence as a follow-up to Trend Micro’s October 2014 report shows a buzz of activity in the first quarter of 2015 from Pawn Storm’s operation with the setup of dozens of exploit URLs and a dozen new command-and-control (C&C) servers targeting NATO members and governments in Europe, Asia and the Middle East.
In a slightly different modus operandi from the usual, Pawn Storm attackers sent out specially-crafted emails designed to trick users into clicking on a malicious link.
Figure 1. Sample spear-phishing email
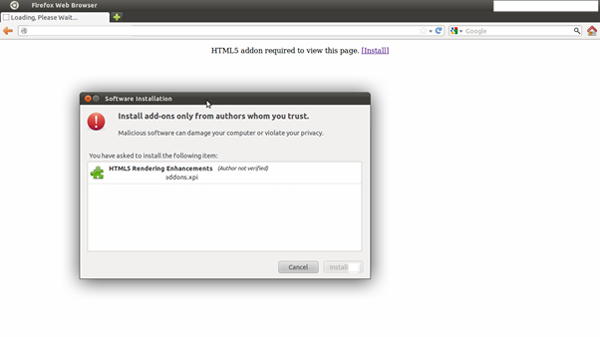
The emails usually have a link to what looks like a legitimate news site. When the target clicks on the link, he will first load a fingerprinting script that feeds back details like OS, time zone, browser and installed plugins to the attackers. When certain criteria are met, the fake news site may respond with a message that an HTML5 plugin has to be installed to view the contents of the site. The add-on in question turns out to be a version of X-Agent or Fysbis spyware if you’re a Linux user, and Sednit if you’re running Windows.
Figure 2. Screenshot of malicious HTML5 plugin
White House Under Attack
Evidence has also shown the White House to be a prime target, with three popular YouTube bloggers being targeted with a Gmail phishing attack on January 26, 2015, four days after the bloggers had interviewed president Obama at the White House. This is a classic island hopping technique, in which attackers focus their efforts not on the actual target but on companies or people that might interact with that target, but which may have weaker security in place.
As per Trend Micro’s s latest Targeted Attack Trends 2014 Annual Report, targeted attacks – otherwise known as advanced persistent threats (APTs), have intensified over the past year alongside newly identified techniques. Trend Micro’s research analysed various forms of APTs, along with the agenda behind these rising assaults and other monitored attack-related command and control (C&C) infrastructure which poses great threats to the computing public.
Organizations and government bodies need to remain vigilant and adopt effective cyber security solutions to adapt to the changing landscape and block phishing and malware downloads. They need to reinforce a custom defence strategy, which uses advanced threat detection technologies and shared intelligence to detect, analyse, and respond to attacks that are invisible to standard security products. Lastly, it is vital to employ user training and education to mitigate the risk of attack.
More information can be found in the Trend Micro blogpost.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!



.png)



