Industrial networks of
energy and ICS integration companies hit by more cyberattacks than any other
industry in H2, 2017
energy and ICS integration companies hit by more cyberattacks than any other
industry in H2, 2017
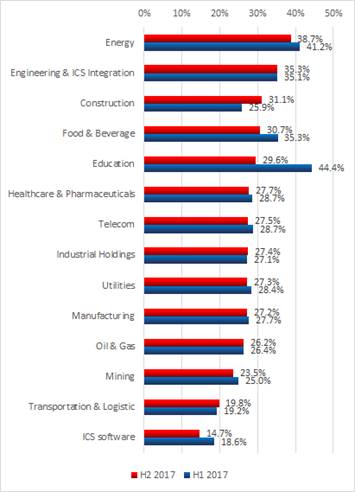
Almost 40% of all
industrial control systems (ICS) in energy organizations protected by Kaspersky
Lab solutions were attacked by malware at least once during the last six months
of 2017, closely followed by 35.3% of engineering & ICS integration networks.
That’s one of the key findings of the latest report from Kaspersky Lab, ‘Threat
Landscape for Industrial Automation Systems in H2 2017’, which found
that the number of attacks on these two sectors noticeably exceeds those on
other industries. Other sectors experienced an average of between 26% and 30%
of ICS computers attacked. The vast majority of detected attacks were
accidental hits.
industrial control systems (ICS) in energy organizations protected by Kaspersky
Lab solutions were attacked by malware at least once during the last six months
of 2017, closely followed by 35.3% of engineering & ICS integration networks.
That’s one of the key findings of the latest report from Kaspersky Lab, ‘Threat
Landscape for Industrial Automation Systems in H2 2017’, which found
that the number of attacks on these two sectors noticeably exceeds those on
other industries. Other sectors experienced an average of between 26% and 30%
of ICS computers attacked. The vast majority of detected attacks were
accidental hits.
The cybersecurity of
industrial facilities remains an issue that can lead to very serious
consequences affecting industrial processes, as well as businesses losses.
While analyzing the threat landscape in different industries, Kaspersky Lab ICS
CERT recorded that nearly all industries regularly experience cyberattacks on
their ICS computers.
industrial facilities remains an issue that can lead to very serious
consequences affecting industrial processes, as well as businesses losses.
While analyzing the threat landscape in different industries, Kaspersky Lab ICS
CERT recorded that nearly all industries regularly experience cyberattacks on
their ICS computers.
However, two
industries were attacked more than others – energy organizations (38.7%) and
engineering & ICS integration businesses (35.3%). The sector that
demonstrated the most noticeable growth of ICS computers attacked during H2
2017 (compared to H1 2017) was construction, with 31.1%. For all other
industries in question (manufacturing, transportation, utilities, food,
healthcare etc.) the proportion of attacked computers ranged from 26% to 30% on
average.
industries were attacked more than others – energy organizations (38.7%) and
engineering & ICS integration businesses (35.3%). The sector that
demonstrated the most noticeable growth of ICS computers attacked during H2
2017 (compared to H1 2017) was construction, with 31.1%. For all other
industries in question (manufacturing, transportation, utilities, food,
healthcare etc.) the proportion of attacked computers ranged from 26% to 30% on
average.
According to experts,
the energy sector was one of the first industries that started to widely use
various automation solutions and is now one of the most computerized.
Cybersecurity incidents and targeted attacks over the past couple of years,
along with regulatory initiatives make a strong case for the power and energy
companies to start adopting cybersecurity products and measures for their
operational technology (OT) systems.
the energy sector was one of the first industries that started to widely use
various automation solutions and is now one of the most computerized.
Cybersecurity incidents and targeted attacks over the past couple of years,
along with regulatory initiatives make a strong case for the power and energy
companies to start adopting cybersecurity products and measures for their
operational technology (OT) systems.
Moreover, the modern
power grid is one of the most extensive systems of interconnected industrial
objects, with a large number of computers connected to the network and a
relatively high degree of exposure to cyber threats, as demonstrated by
Kaspersky Lab ICS CERT statistics. In turn, the high percentage of attacked ICS
computers in engineering and ICS Integration businesses is another serious
problem given the fact that the supply chain attack vector has been used in
some devastating attacks in recent years.
power grid is one of the most extensive systems of interconnected industrial
objects, with a large number of computers connected to the network and a
relatively high degree of exposure to cyber threats, as demonstrated by
Kaspersky Lab ICS CERT statistics. In turn, the high percentage of attacked ICS
computers in engineering and ICS Integration businesses is another serious
problem given the fact that the supply chain attack vector has been used in
some devastating attacks in recent years.
The relatively high
percentage of attacked ICS computers in the construction industry compared to
H1 2017 could indicate that these organizations are not necessarily mature
enough to pay the required attention to the protection of industrial computers.
Their computerized automation systems might be relatively new and an industrial
cyber security culture is still to be developed in these organizations.
percentage of attacked ICS computers in the construction industry compared to
H1 2017 could indicate that these organizations are not necessarily mature
enough to pay the required attention to the protection of industrial computers.
Their computerized automation systems might be relatively new and an industrial
cyber security culture is still to be developed in these organizations.
The lowest percentage
of ICS attacks has been found in enterprises specializing in developing ICS
software – 14.7%, meaning that their ICS research / development laboratories,
testing platforms, demo stands and training environment are also being attacked
by malicious software, although not as often as the ICS computers of industrial
enterprises. Kaspersky Lab ICS CERT experts point to the significance of ICS
vendors’ security, because the consequences of an attack spreading over the
vendor’s partner ecosystem and customer base could be very dramatic, as was
seen during the exPetr malware epidemic, for instance.
of ICS attacks has been found in enterprises specializing in developing ICS
software – 14.7%, meaning that their ICS research / development laboratories,
testing platforms, demo stands and training environment are also being attacked
by malicious software, although not as often as the ICS computers of industrial
enterprises. Kaspersky Lab ICS CERT experts point to the significance of ICS
vendors’ security, because the consequences of an attack spreading over the
vendor’s partner ecosystem and customer base could be very dramatic, as was
seen during the exPetr malware epidemic, for instance.
Percentage of ICS
computers attacked in different industries*, H1 vs H2 2017
computers attacked in different industries*, H1 vs H2 2017
Among the new trends
of 2017, Kaspersky Lab ICS CERT researchers have discovered a rise in mining
attacks on ICS. This growth trend began in September, along with an increase in
the cryptocurrency market and miners in general. But in the case of industrial
enterprises, this type of attack can pose a greater threat by creating a
significant load on computers and, as a result, negatively affecting the
operation of the enterprise’s ICS components and threatening their stability.
Overall, during the period from February 2017 to January 2018, cryptocurrency
mining programs attacked 3.3% of industrial automation system computers, in
most cases accidentally.
of 2017, Kaspersky Lab ICS CERT researchers have discovered a rise in mining
attacks on ICS. This growth trend began in September, along with an increase in
the cryptocurrency market and miners in general. But in the case of industrial
enterprises, this type of attack can pose a greater threat by creating a
significant load on computers and, as a result, negatively affecting the
operation of the enterprise’s ICS components and threatening their stability.
Overall, during the period from February 2017 to January 2018, cryptocurrency
mining programs attacked 3.3% of industrial automation system computers, in
most cases accidentally.
Other highlights from
the report include:
the report include:
· Kaspersky Lab products blocked attempted infections
on 37.8% of ICS computers protected by them. This is 1.4
percentage points less than in the second half of 2016.
on 37.8% of ICS computers protected by them. This is 1.4
percentage points less than in the second half of 2016.
· The internet remains the main source of infection
with 22.7% of ICS computers attacked. This is 2.3% higher than
in the first six months of the year. The percentage of blocked web-borne
attacks In Europe and North America is substantially lower than elsewhere.
with 22.7% of ICS computers attacked. This is 2.3% higher than
in the first six months of the year. The percentage of blocked web-borne
attacks In Europe and North America is substantially lower than elsewhere.
· The top five countries by percentage of ICS computers attacked has
remained unchanged since H1 2017 and includes Vietnam (69.6%), Algeria (66.2%),
Morocco (60.4%), Indonesia (60.1%), and China (59.5%).
remained unchanged since H1 2017 and includes Vietnam (69.6%), Algeria (66.2%),
Morocco (60.4%), Indonesia (60.1%), and China (59.5%).
· In the second half of 2017, the number of different
malware modifications detected by Kaspersky Lab solutions installed on
industrial automation systems increased from 18 thousand to over 18.9
thousand.
malware modifications detected by Kaspersky Lab solutions installed on
industrial automation systems increased from 18 thousand to over 18.9
thousand.
· In 2017, 10.8% of all ICS systems
were attacked by botnet agents, a malware that secretly infects machines and
includes them in a botnet network for remote command execution; the main
sources of attacks like this were the internet, removable media and email
messages.
were attacked by botnet agents, a malware that secretly infects machines and
includes them in a botnet network for remote command execution; the main
sources of attacks like this were the internet, removable media and email
messages.
· In 2017, Kaspersky Lab ICS CERT identified 63
vulnerabilities in industrial systems and IIoT/IoT systems, and 26 of
them have been fixed by vendors.
vulnerabilities in industrial systems and IIoT/IoT systems, and 26 of
them have been fixed by vendors.
“The results of our
research into attacked ICS computers in various industries have surprised us.
For example, the high percentage of ICS computers attacked in power and energy
companies demonstrated that the enterprises’ effort to ensure cybersecurity of
their automation systems after some serious incidents in the industry is not
enough, and there are multiple loopholes still there that cybercriminals can
use,”
said Evgeny Goncharov, Head of Kaspersky Lab ICS CERT.
research into attacked ICS computers in various industries have surprised us.
For example, the high percentage of ICS computers attacked in power and energy
companies demonstrated that the enterprises’ effort to ensure cybersecurity of
their automation systems after some serious incidents in the industry is not
enough, and there are multiple loopholes still there that cybercriminals can
use,”
said Evgeny Goncharov, Head of Kaspersky Lab ICS CERT.
“Overall, in
comparison with 2016 we have seen a slight decline in the number of ICS
attacks. This probably indicates that, generally, enterprises have started to
pay a bit more attention to ICS cybersecurity issues, and are auditing the
industrial segments of their networks, training employees, etc. It is a good
sign, because it’s highly important for businesses to take proactive measures
in order to avoid firefighting in future,” he adds.
comparison with 2016 we have seen a slight decline in the number of ICS
attacks. This probably indicates that, generally, enterprises have started to
pay a bit more attention to ICS cybersecurity issues, and are auditing the
industrial segments of their networks, training employees, etc. It is a good
sign, because it’s highly important for businesses to take proactive measures
in order to avoid firefighting in future,” he adds.
Kaspersky Lab ICS CERT
recommends the following technical measures to be taken:
recommends the following technical measures to be taken:
· Regularly update operating systems, application
software and security solutions on systems that are part of the enterprise’s
industrial network.
software and security solutions on systems that are part of the enterprise’s
industrial network.
· Restrict network traffic on ports and protocols used
on the edge routers and inside organization’s OT networks.
on the edge routers and inside organization’s OT networks.
· Audit ICS component access control in the enterprise’s
industrial network and at its boundaries.
industrial network and at its boundaries.
· Deploy dedicated endpoint protection solutions onto
ICS servers, workstations and HMIs to secure OT and industrial infrastructure
from random cyberattacks.
ICS servers, workstations and HMIs to secure OT and industrial infrastructure
from random cyberattacks.
· Deploy network traffic monitoring, analysis and
detection solutions for better protection from targeted attacks.
detection solutions for better protection from targeted attacks.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!