Fake cryptocurrency trading apps on Google Play caught harvesting credentials
SINGAPORE, 24 October 2017– ESET, a leading global cybersecurity company from the European Union, today announces that users of the popular cryptocurrency exchange Poloniex have been the target of two credential stealing apps, discovered on Google Play disguised as legitimate mobile apps of the exchange. Apart from harvesting Poloniex login credentials, the crooks behind the fake apps have also tried to trick victims into granting them access to their Gmail accounts.
Poloniex is one of the world’s leading cryptocurrency exchanges with more than 100 cryptocurrencies to buy and trade in. That alone makes it an attractive target for fraudsters of all kinds, but in this case, it was its lack of official mobile app that the criminals took advantage of.
With all the hype around cryptocurrencies, cybercriminals are trying to grasp whatever new opportunity they can – be it hijacking common users’ computing power to mine cryptocurrencies via browsers or by infecting unpatched machines, or various scam schemes utilizing fake phishing websites and apps.
The malicious apps
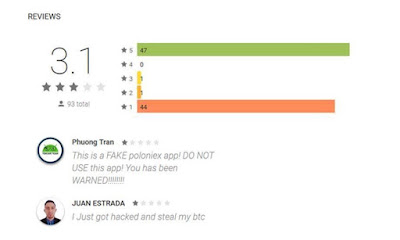
The first of the malicious apps sneaked into Google Play using the name “POLONIEX”, brought by the developer “Poloniex”. Between 28 August and 19 September, the app was installed by up to 5000 users, even despite mixed ratings and bad written reviews.
The second app, “POLONIEX EXCHANGE” by the developer “POLONIEX COMPANY”, appeared on Google Play on 15 October and reached up to 500 installs before being removed from the store upon ESET’s notification.
Apart from notifying Google, we also informed Poloniex of the malicious imposters.
Figure 1 – The fake apps as discovered on Google Play
Figure 2 – Google Play reviews for one of the apps
How do they operate?
To successfully take over a Poloniex account using one of the malicious apps, the attackers first need to obtain credentials for the account. Afterwards, they need to gain access to the email account associated with the compromised Poloniex account to control notifications about unauthorized logins and transactions. Finally, the attackers need to make their app appear functional to lower any suspicion they might have raised in the process.
Both apps use the same method to achieve this.
The credential stealing takes place right after the user launches one of the apps. The malicious app displays a bogus screen requesting Poloniex login credentials (Figure 3). If the user enters the credentials and clicks on “sign in”, the credentials are sent to the attackers.
In case the user doesn’t have 2-factor authentication (2FA) enabled on their Poloniex account, attackers now have access to that account. This means the attackers can carry out transactions on the user’s behalf, change their settings, or even lock them out of their account by changing their password.
If the user does use 2FA, their account is safe from the intruders. This is because Poloniex offers its users 2FA via Google Authenticator, which generates random login codes that are sent to users via text, voice call, or the Google Authenticator app – none of which can be accessed by the attackers.
Figure 3 – Bogus login form harvesting Poloniex credentials
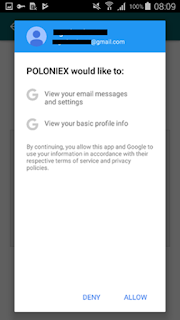
If the crooks were successful, they start working on accessing the user’s Gmail account. The user sees an activity seemingly on behalf of Google, asking them to sign in with their Google account “for two-step security check” (Figure 4). After the user clicks on “sign in”, the malicious app asks for a permission to view user’s email messages and settings and basic profile info (Figure 5). If the user grants the permissions, the app gains access to their inbox.
With access to the user’s Poloniex account as well as associated Gmail account, the attackers can make transactions on the user’s behalf and erase any notifications about unauthorized login and transactions from their inbox.
Figure 4 – Activity impersonating Google requesting the user to sign in to Gmail
Figure 5 – The malicious app requesting access to emails
Finally, to make their app appear functional, the malicious app directs the user to the mobile version of the legitimate Poloniex website, which requests the user to sign in (Figure 6). After the user logs in, they can begin using the legitimate Poloniex website. From then on, the app will only open the legitimate website each time it’s launched.
Figure 6 –Mobile version of the legitimate Poloniex website opened by the malicious app
Another way in which the attackers try to go unnoticed – in this case, by security analysts – is by masking the domains to which stolen credentials are sent using Unicode character tricks. As a result, the domains hxxp://połoniex.com and hxxp://poloniėx.com/ might appear like legitimate Poloniex domains when manually reviewed.
How to protect yourself?
If you’re a Poloniex user and have installed any of these malicious apps on your device, start with uninstalling them. Make sure to change both your Poloniex and Gmail password and consider enabling 2-factor-authentication wherever possible.
Here’s what you can do to avoid falling victim to fraudsters in the future:
- Make sure the service you’re using really offers a mobile app – if that’s the case, the app should be linked on the service’s official website
- Pay attention to app ratings and reviews
- Be cautious of third party apps triggering alerts and windows appearing to be connected to Google – misusing users’ trust towards Google is a popular trick among cybercriminals
- Use 2FA for an additional (and often crucial) layer of security
- Use a reliable mobile security solution; ESET detects the credential stealers as Android/FakeApp.GV
IoCs
|
Package Name
|
Hash
|
|
com.poloniex.exchange
|
89BE9AF09BB3B2CAD9EAF88FE0EF175E5F150044
|
|
com.poloniexap.poloniex
|
427CBAFD6E28C50708E26A481A9C8665C3315BCD
|
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint and mobile security, to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give consumers and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real-time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D centers worldwide, ESET becomes the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003. For more information visit www.eset.com or follow us on LinkedIn, Facebook andTwitter.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!