The Petya variant
of ransomware utilizes a similar, if not somewhat modified, version of
EternalBlue exploit—as used by the Wannacry ransomware in May this year—to
spread to all active end-points on the affected network.
of ransomware utilizes a similar, if not somewhat modified, version of
EternalBlue exploit—as used by the Wannacry ransomware in May this year—to
spread to all active end-points on the affected network.
What is Petya, and how does it work?
The Petya variant
of ransomware is different from Wannacry as Petya impacts the Master Boot
Record (MBR). Petya first reboots the computers, and then encrypts the hard
drive’s file table (MFT), which renders the MBR inoperable. From this point
forwards, it restricts access to the system by seizing information of file
names, sizes and location on the physical disk. Finally, Petya replaces the
computer’s MBR with its own code, which displays the ransom note once the
system is powered up.
of ransomware is different from Wannacry as Petya impacts the Master Boot
Record (MBR). Petya first reboots the computers, and then encrypts the hard
drive’s file table (MFT), which renders the MBR inoperable. From this point
forwards, it restricts access to the system by seizing information of file
names, sizes and location on the physical disk. Finally, Petya replaces the
computer’s MBR with its own code, which displays the ransom note once the
system is powered up.
There has been
report in Australia of businesses affected by the Petya ransomware, namely the Tasmanian
Cadbury chocolate factory, global law firm DLA
Piper, and the Jawaharlal
Nehru Port Trust. If the Wannacry
attacks in May this year are any indication, the Petya ransomware could
potentially be spread worldwide within the next 72 hours.
report in Australia of businesses affected by the Petya ransomware, namely the Tasmanian
Cadbury chocolate factory, global law firm DLA
Piper, and the Jawaharlal
Nehru Port Trust. If the Wannacry
attacks in May this year are any indication, the Petya ransomware could
potentially be spread worldwide within the next 72 hours.
The Rise of Ransomware-as-a-service
The Petya variant
of ransomware also gives rise to a new—if not unsavory—business model:
Ransomware-as-a-service (RaaS). While there is still some debate as to whether
it is a variant of Petya, GoldenEye, or a new version of Wannacry, we can be
sure that it was definitely not from the original author of the Petya variant
of ransomware. This means that hackers actually purchased the source code and
used the models to create the attack.
of ransomware also gives rise to a new—if not unsavory—business model:
Ransomware-as-a-service (RaaS). While there is still some debate as to whether
it is a variant of Petya, GoldenEye, or a new version of Wannacry, we can be
sure that it was definitely not from the original author of the Petya variant
of ransomware. This means that hackers actually purchased the source code and
used the models to create the attack.
While the
potential payouts from ransomed victims can amount in the millions, the actual
ransomware is incredulously cheap, between US$50 to US$150, depending on per
usage or the actual ransomware source-code. The authors then offer their
ransomware on the darknet, and offer a generous portion of the paid ransom
amount to potential distributors, while the author pockets the rest.
potential payouts from ransomed victims can amount in the millions, the actual
ransomware is incredulously cheap, between US$50 to US$150, depending on per
usage or the actual ransomware source-code. The authors then offer their
ransomware on the darknet, and offer a generous portion of the paid ransom
amount to potential distributors, while the author pockets the rest.
Acronis Active Protection™ – Proven Against
Petya
Petya
In tests conducted
yesterday on the Petya ransomware, we can confirm that our Acronis Active
Protection™ can effectively protect users from attacks.
yesterday on the Petya ransomware, we can confirm that our Acronis Active
Protection™ can effectively protect users from attacks.
Anti-virus
solutions utilize signature-based detection, and targets a specific
characteristics of the virus in order to prevent it from affecting the system.
Acronis Active Protection utilizes heuristics detection, which monitors a set
of processes and procedures that ransomware and malware follow through during
an attack.
solutions utilize signature-based detection, and targets a specific
characteristics of the virus in order to prevent it from affecting the system.
Acronis Active Protection utilizes heuristics detection, which monitors a set
of processes and procedures that ransomware and malware follow through during
an attack.
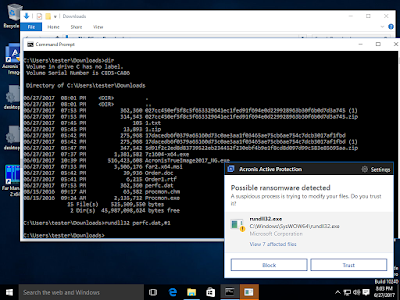
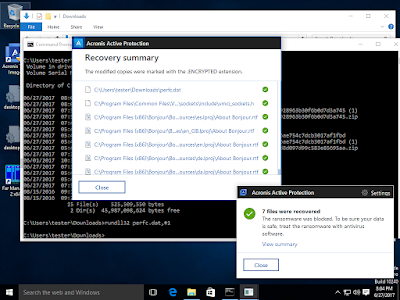
|
Detection at the
point of attack in real time |
|
Recovery of
encrypted files |
The Acronis Active Protection has been independently tested by MRG
Effitas and AV
Test, and has been proven effective against
the threat of ransomware, and is now available with Acronis
True image 2017 New Generation
for consumers, as well as Acronis Backup
12.5 for businesses.
Effitas and AV
Test, and has been proven effective against
the threat of ransomware, and is now available with Acronis
True image 2017 New Generation
for consumers, as well as Acronis Backup
12.5 for businesses.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!