This is one of the first instances in which
an entire Android market gets infected by the same malware
an entire Android market gets infected by the same malware
SINGAPORE,
26 JULY 2017 – ESET
researchers discovered that CepKutusu.com, a Turkish alternative Android app
store was spreading malware under the guise of every offered Android app.
26 JULY 2017 – ESET
researchers discovered that CepKutusu.com, a Turkish alternative Android app
store was spreading malware under the guise of every offered Android app.
When users
browsed the Turkish alternative app store and proceeded to download an app, the
“Download now” button led to banking malware instead of the desired app. A few
weeks after ESET researchers turned to the store’s operator with the discovery
of the attack, the store ceased the malicious activity.
browsed the Turkish alternative app store and proceeded to download an app, the
“Download now” button led to banking malware instead of the desired app. A few
weeks after ESET researchers turned to the store’s operator with the discovery
of the attack, the store ceased the malicious activity.
Interestingly,
although ESET researchers found the misdirection from a legitimate app to the
malicious one to be general – meaning that every single app was set to be
replaced with the banking malware, the crooks behind the campaign added an
exception. Probably to increase the chance to stay longer under the radar, they
introduced a seven-day window of not serving malware after a malicious
download. In practice, after the user downloads the infected app, a cookie is
set to prevent the malicious system from prevailing, leading to the user being
served clean links for next seven days. After this period passes, the user gets
redirected to malware once they try to download any application from the store.
although ESET researchers found the misdirection from a legitimate app to the
malicious one to be general – meaning that every single app was set to be
replaced with the banking malware, the crooks behind the campaign added an
exception. Probably to increase the chance to stay longer under the radar, they
introduced a seven-day window of not serving malware after a malicious
download. In practice, after the user downloads the infected app, a cookie is
set to prevent the malicious system from prevailing, leading to the user being
served clean links for next seven days. After this period passes, the user gets
redirected to malware once they try to download any application from the store.
The
malicious app distributed by the store at the time of the investigation was
remotely controlled banking malware capable of intercepting and sending SMS,
displaying fake activity, as well as downloading and installing other apps.
malicious app distributed by the store at the time of the investigation was
remotely controlled banking malware capable of intercepting and sending SMS,
displaying fake activity, as well as downloading and installing other apps.
When
installed, the malware doesn’t mimic the app the user intended to install.
Instead, it imitates Flash Player.
installed, the malware doesn’t mimic the app the user intended to install.
Instead, it imitates Flash Player.
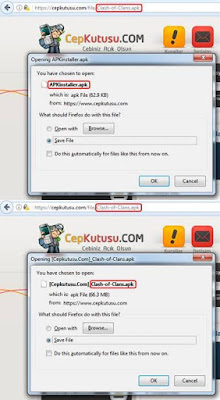
Figure 1 –
The malicious app served to a user who thinks they are downloading the Clash of
Clans game and the legitimate game served to the same user within the seven day
period, respectively.
The malicious app served to a user who thinks they are downloading the Clash of
Clans game and the legitimate game served to the same user within the seven day
period, respectively.
To gain
more insight on this attack and its wider implications, we turned to Lukáš Štefanko, Malware Researcher at ESET,
who specializes in Android malware and who discovered the malware-distributing
app store.
more insight on this attack and its wider implications, we turned to Lukáš Štefanko, Malware Researcher at ESET,
who specializes in Android malware and who discovered the malware-distributing
app store.
An app
store serving its customers with malware on a mass scale – that sounds like a
big threat. On the other hand, serving Flash Player instead of whatever
customers wanted – that’s a rather thin disguise… What’s your take on this?
store serving its customers with malware on a mass scale – that sounds like a
big threat. On the other hand, serving Flash Player instead of whatever
customers wanted – that’s a rather thin disguise… What’s your take on this?
First, let
me say that this is the first time I hace seen an entire Android market
infected like that. Within the Windows ecosystem and in browsers, this
technique is known to have been used for some time but in the Android
ecosystem, it’s really a new attack vector.
me say that this is the first time I hace seen an entire Android market
infected like that. Within the Windows ecosystem and in browsers, this
technique is known to have been used for some time but in the Android
ecosystem, it’s really a new attack vector.
As for the
impact, what we saw in this particular case was most probably a test. The
crooks misused their control of the app store in the simplest manner. Replacing
the links to all apps with a link to a single malicious app requires virtually no
effort – but it also gives the store’s customers a fair chance to detect the
scam. If you got lured into downloading a popular game and ended up with Flash
Player instead… I think you’d uninstall it straight away and report the issue,
right?
impact, what we saw in this particular case was most probably a test. The
crooks misused their control of the app store in the simplest manner. Replacing
the links to all apps with a link to a single malicious app requires virtually no
effort – but it also gives the store’s customers a fair chance to detect the
scam. If you got lured into downloading a popular game and ended up with Flash
Player instead… I think you’d uninstall it straight away and report the issue,
right?
This might
explain why we have seen only a few hundred infections.
explain why we have seen only a few hundred infections.
From this
point of view, it doesn’t sound like a big deal …
point of view, it doesn’t sound like a big deal …
Well, like
I said, it was probably a test. I can imagine a scenario in which the crooks
who control the store’s back end append a malicious functionality to each of
the apps in the store. Serving those interested in a particular game with a
trojanised version of that game… That would remove the biggest red flag and
the number of victims might rise significantly.
I said, it was probably a test. I can imagine a scenario in which the crooks
who control the store’s back end append a malicious functionality to each of
the apps in the store. Serving those interested in a particular game with a
trojanised version of that game… That would remove the biggest red flag and
the number of victims might rise significantly.
As for the
attribution of this attack – have you found any traces?
attribution of this attack – have you found any traces?
There are
three possible scenarios here: an app store built with the intention to spread
malware; a legitimate app store turned malicious by an employee with bad
intentions; and a legitimate app store becoming a victim of a remote attacker.
three possible scenarios here: an app store built with the intention to spread
malware; a legitimate app store turned malicious by an employee with bad
intentions; and a legitimate app store becoming a victim of a remote attacker.
As for
scenarios two and three, I would think that such an attack would not go
unnoticed by a legitimate store. User complaints, suspicious server logs and
changes in code should be sufficient indicators for its operators…. The more that
the malware was being distributed via the store for weeks. Also of interest in
this regard is that we contacted the store operators with our findings but have
not received any reaction.
scenarios two and three, I would think that such an attack would not go
unnoticed by a legitimate store. User complaints, suspicious server logs and
changes in code should be sufficient indicators for its operators…. The more that
the malware was being distributed via the store for weeks. Also of interest in
this regard is that we contacted the store operators with our findings but have
not received any reaction.
How to
protect yourself
protect yourself
Recommendations
by ESET’s Lukáš Štefanko:
by ESET’s Lukáš Štefanko:
- If possible, always favour downloading apps from
official app stores. This piece of advice is infinitely repeated for a
good reason – there is no guarantee of any security measures in
alternative app stores, making them a great place for malware authors to
spread their “work”, and not just via single malicious apps, but also on a
mass scale, as illustrated in this case. - Be cautious when downloading content from the
internet. Pay attention to anything suspicious in file name, size and
extension – this is where many threats can still be recognized and avoided
in time. - Use a reliable mobile security solution
to protect you from the latest threats. As for the threat hidden in the
alternative app store, ESET detects it as Android/Spy.Banker.IE and prevents it from
getting downloaded.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!