WannaCry/Wcry Ransomware: How to Defend against It
An
unprecedented wave of ransomware infections is hitting organizations in all
industries around the world. The culprit: the WannaCry/WCry ransomware
(detected by Trend Micro as RANSOM_WANA.A and RANSOM_WCRY.I).
unprecedented wave of ransomware infections is hitting organizations in all
industries around the world. The culprit: the WannaCry/WCry ransomware
(detected by Trend Micro as RANSOM_WANA.A and RANSOM_WCRY.I).
Trend
Micro has been tracking WannaCry since its
emergence in the wild in April 2017. Trend Micro™ XGen™ security has been protecting users from this and other threats
using techniques like behavioral analysis and high fidelity machine learning.
Here’s what users and enterprises need to know about this widespread threat and
what can be done to defend against it.
Micro has been tracking WannaCry since its
emergence in the wild in April 2017. Trend Micro™ XGen™ security has been protecting users from this and other threats
using techniques like behavioral analysis and high fidelity machine learning.
Here’s what users and enterprises need to know about this widespread threat and
what can be done to defend against it.
What happened?
Several
firms in Europe were the first to report having their mission-critical Windows systems
locked, showing a ransom note. This quickly developed into one of the most
widespread ransomware outbreaks currently affecting a large number of
organizations around the world. Some affected organizations had to take their
IT infrastructure offline, with victims in the healthcare industry experiencing
delayed operations and forced to turn away patients until processes could be
re-established.
firms in Europe were the first to report having their mission-critical Windows systems
locked, showing a ransom note. This quickly developed into one of the most
widespread ransomware outbreaks currently affecting a large number of
organizations around the world. Some affected organizations had to take their
IT infrastructure offline, with victims in the healthcare industry experiencing
delayed operations and forced to turn away patients until processes could be
re-established.
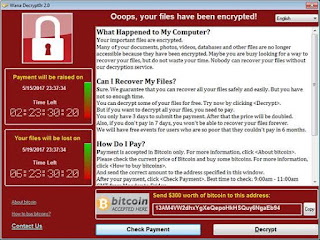
Figure 1: One of WannaCry’s ransom notes
Who is affected?
This
variant of the WannaCry ransomware attacks older Windows-based systems, and is
leaving a trail of significant damage in its wake. Based on Trend Micro’s
initial telemetry, Europe has the highest detections for the WannaCry
ransomware. The Middle East, Japan, and several countries in the Asia Pacific
(APAC) region showing substantial infection rates as well.
variant of the WannaCry ransomware attacks older Windows-based systems, and is
leaving a trail of significant damage in its wake. Based on Trend Micro’s
initial telemetry, Europe has the highest detections for the WannaCry
ransomware. The Middle East, Japan, and several countries in the Asia Pacific
(APAC) region showing substantial infection rates as well.
WannaCry’s
infections were seen affecting various enterprises, including those in
healthcare, manufacturing, energy (oil and gas), technology, food and beverage,
education, media and communications, and government. Due to the widespread
nature of this campaign, it does not appear to be targeting specific victims or
industries.
infections were seen affecting various enterprises, including those in
healthcare, manufacturing, energy (oil and gas), technology, food and beverage,
education, media and communications, and government. Due to the widespread
nature of this campaign, it does not appear to be targeting specific victims or
industries.
What does WannaCry ransomware do?
WannaCry
ransomware targets and encrypts 176 file types. Some of the file types WannaCry
targets are database, multimedia and archive files, as well as Office
documents. In its ransom note, which supports 27 languages, it initially
demands US$300 worth of Bitcoins from its victims—an amount that increases incrementally
after a certain time limit. The victim is also given a seven-day limit before
the affected files are deleted—a commonly used fear-mongering tactic.
ransomware targets and encrypts 176 file types. Some of the file types WannaCry
targets are database, multimedia and archive files, as well as Office
documents. In its ransom note, which supports 27 languages, it initially
demands US$300 worth of Bitcoins from its victims—an amount that increases incrementally
after a certain time limit. The victim is also given a seven-day limit before
the affected files are deleted—a commonly used fear-mongering tactic.
WannaCry leverages CVE-2017-0144, a vulnerability in Server Message Block,
to infect systems. The security flaw is attacked using an exploit leaked by the Shadow Brokers group—the “EternalBlue” exploit, in particular. Microsoft’s
Security Response Center (MSRC) Team addressed the vulnerability via MS17-010 released March, 2017.
to infect systems. The security flaw is attacked using an exploit leaked by the Shadow Brokers group—the “EternalBlue” exploit, in particular. Microsoft’s
Security Response Center (MSRC) Team addressed the vulnerability via MS17-010 released March, 2017.
What
makes WannaCry’s impact pervasive is its capability to propagate. Its worm-like
behavior allows WannaCry to spread across networks, infecting connected systems
without user interaction. All it takes is for one user on a network to be
infected to put the whole network at risk. WannaCry’s propagation capability is
reminiscent of ransomware families like SAMSAM, HDDCryptor, and several variants of Cerber—all
of which can infect systems and servers connected to the network.
makes WannaCry’s impact pervasive is its capability to propagate. Its worm-like
behavior allows WannaCry to spread across networks, infecting connected systems
without user interaction. All it takes is for one user on a network to be
infected to put the whole network at risk. WannaCry’s propagation capability is
reminiscent of ransomware families like SAMSAM, HDDCryptor, and several variants of Cerber—all
of which can infect systems and servers connected to the network.
What can you do?
WannaCry
highlights the real-life impact of ransomware: crippled systems, disrupted
operations, marred reputations, and the financial losses resulting from being
unable to perform normal business functions—not to mention the cost of incident
response and clean up.
highlights the real-life impact of ransomware: crippled systems, disrupted
operations, marred reputations, and the financial losses resulting from being
unable to perform normal business functions—not to mention the cost of incident
response and clean up.
Here
are some of the solutions and best practices that organizations can adopt and
implement to safeguard their systems from threats like WannaCry:
are some of the solutions and best practices that organizations can adopt and
implement to safeguard their systems from threats like WannaCry:
· The ransomware exploits a vulnerability in SMB
server. Patching is critical for defending against attacks that exploit
security flaws. A patch for this issue is available for Windows systems, including those no longer supported
by Microsoft. When organizations
can’t patch directly, using a virtual patch can help mitigate the threat
server. Patching is critical for defending against attacks that exploit
security flaws. A patch for this issue is available for Windows systems, including those no longer supported
by Microsoft. When organizations
can’t patch directly, using a virtual patch can help mitigate the threat
· Deploying firewalls and detection and intrusion prevention systems can help reduce the spread of this threat. A security system
that can proactively monitor attacks in the
network also helps stops these threats
that can proactively monitor attacks in the
network also helps stops these threats
· Aside from using an exploit to spread,
WannaCry reportedly also uses spam as entry point. Identifying red flags on socially
engineered spam emails that contain system
exploits helps. IT and system administrators should deploy security mechanisms that can
protect endpoints from email-based malware
WannaCry reportedly also uses spam as entry point. Identifying red flags on socially
engineered spam emails that contain system
exploits helps. IT and system administrators should deploy security mechanisms that can
protect endpoints from email-based malware
· WannaCry drops several malicious components in
the system to conduct its encryption routine. Application control based on a whitelist can prevent unwanted and unknown
applications from executing. Behavior monitoring can block unusual modifications to the system. Ransomware uses a
number of techniques to infect a system; defenders should do the same to protect their systems
the system to conduct its encryption routine. Application control based on a whitelist can prevent unwanted and unknown
applications from executing. Behavior monitoring can block unusual modifications to the system. Ransomware uses a
number of techniques to infect a system; defenders should do the same to protect their systems
· WannaCry encrypts files stored on local
systems and network shares. Implementing data categorization helps mitigate any damage incurred from a breach or attack by
protecting critical data in case they are exposed
systems and network shares. Implementing data categorization helps mitigate any damage incurred from a breach or attack by
protecting critical data in case they are exposed
· Network segmentation can also help prevent the spread of this threat internally. Good
network design can help contain the spread of this infection and reduce its
impact on organizations
network design can help contain the spread of this infection and reduce its
impact on organizations
· Disable the SMB protocol on systems that do
not require it. Running unneeded services gives more ways for an attacker to
find an exploitable vulnerability
not require it. Running unneeded services gives more ways for an attacker to
find an exploitable vulnerability
Trend Micro XGen Security detects and blocks
all of WannaCry ransomware’s infection stages
all of WannaCry ransomware’s infection stages
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!