PHISHFUL OF DOLLARS: BEC REMAINS TOP OF THE CHARTS
Business email compromise (BEC) is not going away. Since we initially wrote about BEC back in April 2016, we have continued to report on threat actors using tried and trusted BEC techniques to trick their victims. For example, in May 2015 two separate reports emerged of the theft of $495,000 USD from US Investment company Pomeroy Investment Corp, as well as a spear-phishing scam which resulted in the theft of W-2 information pertaining to 13,000 current and former employees of the Brunswick Corporation. In April 2016 Reuters reported that an unidentified American company had been the victim of BEC which led to the theft of almost $100 million USD.
More recently, Tillage Commodities Fund – a U.S.-based investment company – filed a lawsuit against SS&C Technologies – a provider of financial services technology solutions – as a result of a BEC attempt. Attackers purportedly used a typosquatted email address, spoofing Tillage, to send emails to SS&C employees, who administered the Tillage fund, requesting that wire transfers be made to bank accounts of purported technology companies in Hong Kong. The attack resulted in the theft of $5.9 million from the Tillage fund.
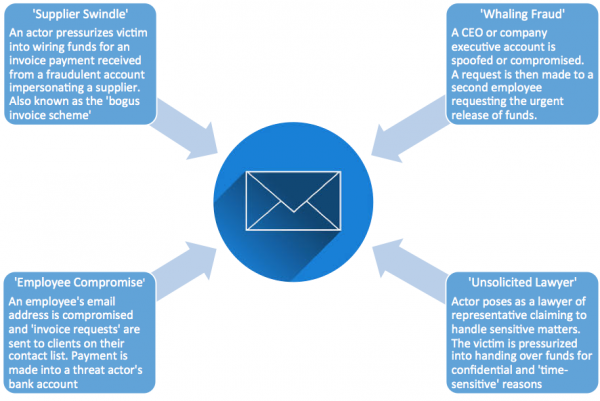
Broadly speaking, we have observed four different types of BEC strategies:
Figure 1: Four main types of BEC attack
In the case of Tillage and SS&C, the attackers appear to have used a variation of the ‘Supplier Swindle’ strategy, effectively tricking SS&C employees into wiring funds to alternative fraudulent accounts. Of broader significance here is the choice of SS&C as a vector for an attack on Tillage Commodities. It is likely that Tillage had been targeted given their reliance on an intermediary party (SS&C) who was responsible for the administration of Tillage assets. This goes to show that despite typo-squatting being a well-established and commonly used tactic, threat actors deem third parties to be vulnerable targets.
Given the relative simplicity of the attacks and the huge potential profits to be made, BEC will highly likely continue to pose a threat to companies and organizations for the foreseeable future. As more and more historical data breaches come into circulation, threat actors will likely use the exposed information for malicious purposes such as such as social engineering, phishing scams, and account takeovers, all of which could be used to facilitate a BEC attack – these techniques are outlined in our recent blog looking at the Industrialized Uses of Breached Data. With this in mind, organizations are advised to adopt a combination of people, process and technology measures to mitigate against BEC attacks, some of which are discussed in our previous blog.
Credits to Digital Shadows.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!