The Industrialized Uses of Breached DataMichael Marriott, security research at Digital Shadows
We have defined industrialization as the growing sophistication of criminal business models, characterized by the automation and replication of previously manual processes. This can be achieved by either increasing role specialization (e.g. malware-as-a-service offerings), or by using new technology.
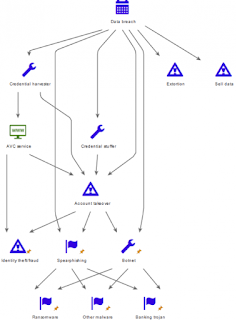
We identified seven key examples of how breached data can currently be industrialized, based on incidents we have detected in the past 24 months:
- Botnets – datasets containing email addresses can be used in the operation of botnets, which can subsequently be used to deliver spam or more malicious pieces of malware
- Post-breach extortion – the Ashley Madison breach highlighted how highly sensitive, or potentially damaging details can be used to blackmail individuals into paying ransom demands
- Credential stuffing – this is a type of brute force attack whereby large sets of credentials are automatically inputted in to websites until a match with an existing account is found
- Credential harvesting – malware such as Pony Loader can be used to steal credentials and/or online currency. The malware is available with a control panel, user management, logging features, a database to manage all the data, and password list to conduct brute force style attacks against less-secure cyber assets
- Spear-phishing – like botnets, threat actors can use breached data in targeted spear-phishing campaigns in order to distribute malware such as banking trojans and ransomware
- Account takeover – although not a new phenomenon, we have repeatedly observed threat actors reusing credentials found in historical breaches to target other accounts using the same passwords
- Automated vending cart (AVC) sites – stolen financial data is not always neatly structured, and cybercriminals may have to work through the processes of searching the data for valuable strings and then structuring the data in a format that is either usable or suitable for sale
Below is a diagram showing the flow of stolen data through the seven industrialized ‘services’ listed above and then onwards to other malicious activities:
Figure 1: The multiple potential uses of one breached dataset
Notably, the graphic above highlights how stolen data that has been used for spear-phishing or in the creation of a botnet can be used to accrue even more data through data-stealing ransomware and banking trojans. This reuse of data creates a “virtuous circle” for the malicious actor where an initial investment in breached data in turn creates a growing pool of stolen information that can be put to a variety of uses.
Looking forward, it not be a stretch to argue that a threat actor could aggregate multiple datasets to build an extensive profile of an individual. Data akin to that exposed in the 2015 Office of Personnel Management breach would reveal an individual’s health, criminal, mental and political background, as well as biometric data such as fingerprints. Ashley Madison data would provide a person’s sexual orientation and behavior, while exposed payment information in other breaches could give the threat actor an understanding of an individual’s financial situation. All this information would provide a threat actor with ample material to exert pressure on that individual – such as for extortion or in the recruitment of a human source.
By taking the perspective of an attacker, we can better understand the risks and threats faced by our clients. This guides our approach towards public data breach incidents, where our analysts consider how attractive and useful a given dataset could be for a malicious actor in order to produce more structured and considered assessments of their severity. You can download a copy of our latest research paper, “Compromised Credentials – Learn From the Exposure of the World’s 1,000 Biggest Companies”, to understand the impact of leaked credentials on organizations.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!