“It is important not to discount the impact of hacktivists on your infrastructure. But by monitoring hacktivist activity, it’s possible to gain a better appreciation of the day-to-day claims and avoid missing something that could potentially become more damaging,’ said Michael Marriott, security research at Digital Shadows.
HACKTIVISM, IT’S NOT ALL DOSING AROUND
Simon Tame | 12 September
2016
2016
Hacktivism isn’t all high levels of low
impact activity. There were a number of hacktivist campaigns we detected in the
last year that seemed to have had little to no effect on their targets at all
(at least from an outside perspective) such as OpSilence, but there are some
operations and actors that have had a demonstrable impact. In my opinion, you
can start to gain an appreciation of the threat level posed by a hacktivist
operation within the first week or so of it being announced. It all depends on
what the objectives are (from an attacker’s perspective), what the targets are,
who is participating and what tools they are using. There are outliers, of
course, and that’s when it becomes a bit more serious.
impact activity. There were a number of hacktivist campaigns we detected in the
last year that seemed to have had little to no effect on their targets at all
(at least from an outside perspective) such as OpSilence, but there are some
operations and actors that have had a demonstrable impact. In my opinion, you
can start to gain an appreciation of the threat level posed by a hacktivist
operation within the first week or so of it being announced. It all depends on
what the objectives are (from an attacker’s perspective), what the targets are,
who is participating and what tools they are using. There are outliers, of
course, and that’s when it becomes a bit more serious.
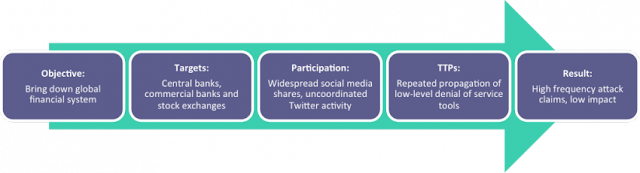
Let’s take a look at what
ingredients are most likely to constitute a low impact to the targeted sectors.
I’m going to use what I consider to be a “cookie cutter” hacktivist operation
as an example – OpIcarus. I know I’ve written about this
before, so forgive me for repeating myself. OpIcarus started with an
ambitious objective (shutting down the global financial system) and reasonably
hard targets (bank websites). It was spread around social media and its
participants called for denial of service attacks against domains belonging to
banks and stock exchanges. It was easily accessible for low capability threat
actors, who were provided with pre-made denial of service scripts to conduct
their attacks. The process is shown in Figure 1.
ingredients are most likely to constitute a low impact to the targeted sectors.
I’m going to use what I consider to be a “cookie cutter” hacktivist operation
as an example – OpIcarus. I know I’ve written about this
before, so forgive me for repeating myself. OpIcarus started with an
ambitious objective (shutting down the global financial system) and reasonably
hard targets (bank websites). It was spread around social media and its
participants called for denial of service attacks against domains belonging to
banks and stock exchanges. It was easily accessible for low capability threat
actors, who were provided with pre-made denial of service scripts to conduct
their attacks. The process is shown in Figure 1.
Figure 1 – Development of OpIcarus operation
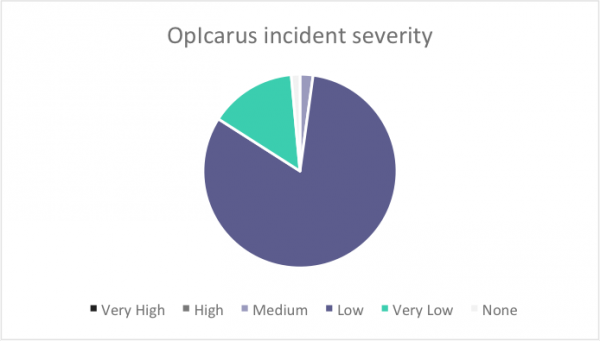
Immediately, OpIcarus participants
had limited the level of impact it could create, based on the targets they had
chosen and the tactics, techniques and procedures they were using. The results
of 141 incidents we published are shown, broken down by severity, in Figure 2.
had limited the level of impact it could create, based on the targets they had
chosen and the tactics, techniques and procedures they were using. The results
of 141 incidents we published are shown, broken down by severity, in Figure 2.
Figure 2 – OpIcarus incidents broken down by
proportion of severity
proportion of severity
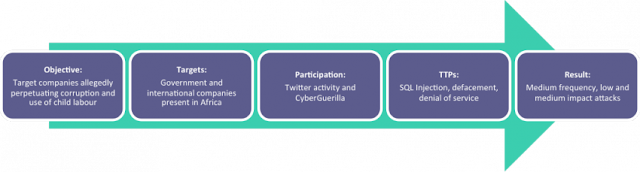
A higher impact occurs when
hacktivists start to become a bit more focused and a lot more coordinated in
their efforts. As well as this, it’s largely dependent on the use of
(potentially) more damaging techniques such as SQL Injection attacks, against
softer targets. I’m going to use an unusual example here, OpAfrica, which was
very similar to your typical hacktivist operation but had a more significant
impact to some targets. The development of OpAfrica is shown in Figure 3.
hacktivists start to become a bit more focused and a lot more coordinated in
their efforts. As well as this, it’s largely dependent on the use of
(potentially) more damaging techniques such as SQL Injection attacks, against
softer targets. I’m going to use an unusual example here, OpAfrica, which was
very similar to your typical hacktivist operation but had a more significant
impact to some targets. The development of OpAfrica is shown in Figure 3.
Figure 3 – Development of OpAfrica operation
Most notably, the likely use of SQL
Injection attacks against vulnerable websites appeared to have made this
operation more damaging than its peers (shown here and here), but
the reasons also included more centralized command (CyberGuerilla) and softer
targets (local government websites in developing countries). Of course, the
capability of some threat actors involved in the operation probably influenced
the successes of this operation.
Injection attacks against vulnerable websites appeared to have made this
operation more damaging than its peers (shown here and here), but
the reasons also included more centralized command (CyberGuerilla) and softer
targets (local government websites in developing countries). Of course, the
capability of some threat actors involved in the operation probably influenced
the successes of this operation.
So when does hacktivism become high
impact? Admittedly, it’s very rare and some might dispute applying the
hacktivist tag in this instance; however, in my opinion there are some cases
(such as the actor Phineas Fisher),
where an ideologically motivated actor demonstrates the capability to conduct
network intrusions and conduct damaging data leakage against their targets.
Phineas Fisher appeared to act against companies perceived as acting
unethcially, and has claimed responsibility for damaging attacks against Hacking Team in Jul
2015 and Gamma Group
International UK Ltd in Aug 2014. These instances are (in my opinion)
more dependent on capability and intent, rather than coordination and tools
used.
impact? Admittedly, it’s very rare and some might dispute applying the
hacktivist tag in this instance; however, in my opinion there are some cases
(such as the actor Phineas Fisher),
where an ideologically motivated actor demonstrates the capability to conduct
network intrusions and conduct damaging data leakage against their targets.
Phineas Fisher appeared to act against companies perceived as acting
unethcially, and has claimed responsibility for damaging attacks against Hacking Team in Jul
2015 and Gamma Group
International UK Ltd in Aug 2014. These instances are (in my opinion)
more dependent on capability and intent, rather than coordination and tools
used.
While I would agree with anyone who
perceives a majority of hacktivist operations and actors as having a relatively
low impact as part of their activity, I think it’s important to acknowledge
where distinctions can be made, particularly in relation to the capability and
intent of hacktivist actors and the selection of vulnerable targets. By
monitoring hacktivist activity, it’s possible to gain a better appreciation of
the day-to-day claims and avoid missing something that could potentially become
more damaging.
perceives a majority of hacktivist operations and actors as having a relatively
low impact as part of their activity, I think it’s important to acknowledge
where distinctions can be made, particularly in relation to the capability and
intent of hacktivist actors and the selection of vulnerable targets. By
monitoring hacktivist activity, it’s possible to gain a better appreciation of
the day-to-day claims and avoid missing something that could potentially become
more damaging.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!