By Tony Perez, General Manager and Vice President of Security Product Group, GoDaddy
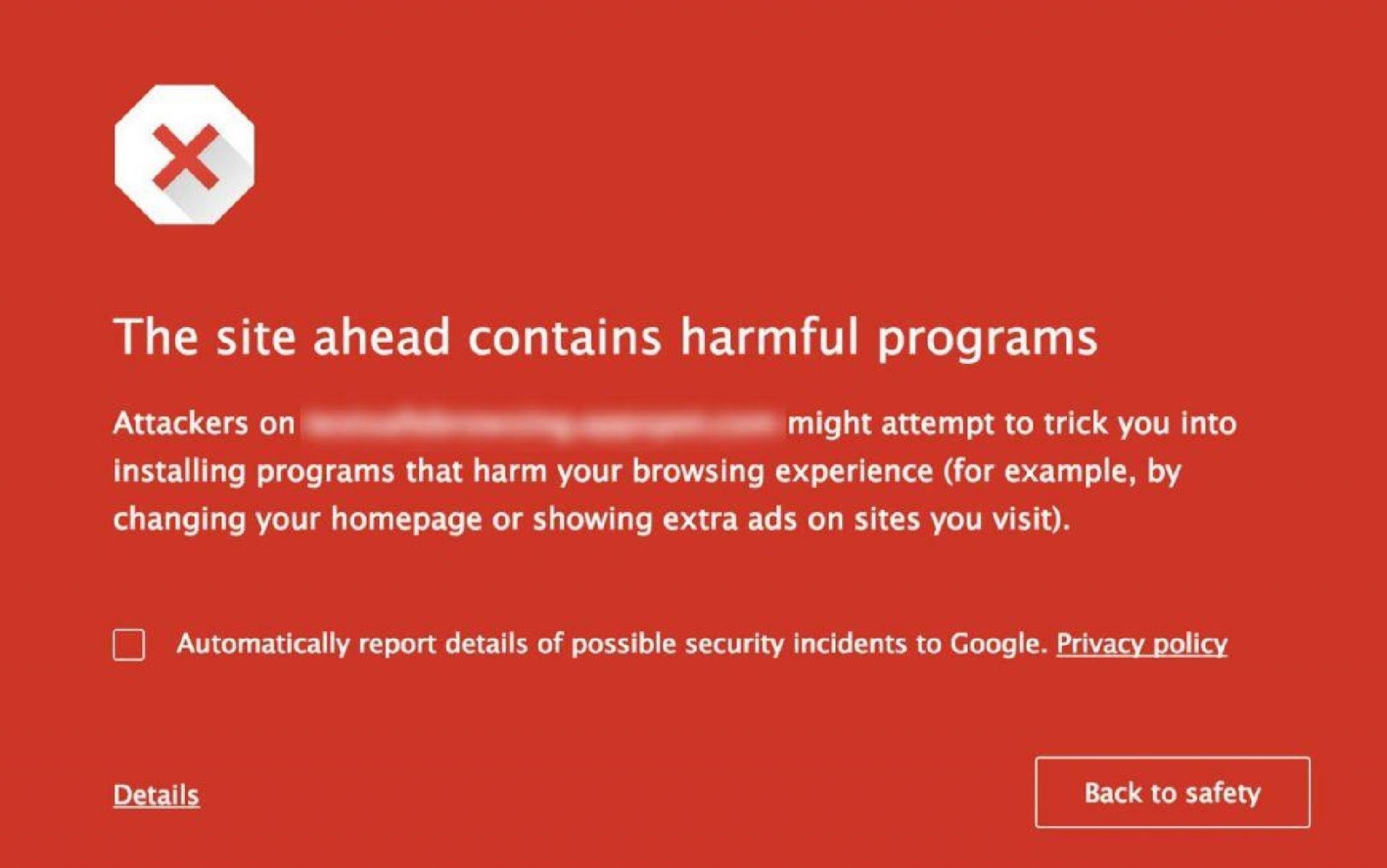
A compromised website can place businesses in the online penalty box in the form of a blacklist. A blacklist is when search engines or internet security companies such as Google, Bing, Norton, or any number of online authorities, discover a site is being used maliciously and flag it as such. It is the process where they introduce a page on the request notifying the user that the site they are going to has been identified as a malicious site. The intention of this categorization is to help protect online consumers from nefarious activity on their respective networks and services.
When a site is blacklisted, traffic to that site often plummets. This drop is attributed to the reduced rankings in the search engine result pages (SERP) because of the blacklist, and a loss of direct traffic as customers are hit with a new interstitial of a potential malicious activity. This is the triple threat for small businesses: first the hacker steals, then a business cannot make money because their website is invisible, then businesses have to rebuild their trust with customers and prospects.
Google, for example, blacklists more than 10,000 websites a day. Getting off the blacklist can make or break a small business. But here is the paradox: getting flagged and blacklisted for having malware effectively shuts down a website affecting the small business owner; not getting flagged when a website has malware dramatically affects online consumers. Organizations like Google, and others, will always plan for the online consumer first.
The best approach is to stay on top of your website’s security to avoid either pitfall. ESET’s State of Cybersecurity in APAC: Small Businesses, Big Threats report found that 35 percent of SMEs find it difficult to justify security spending, especially when other areas of the business need it more. And keeping up on website vulnerabilities is a challenge: While close to half (47 percent) of SMEs had experienced cyber breaches in the past three years, few had basic preventive measures such as cybersecurity awareness programs for employees in place.
An analysis of thousands of website requests reveals sobering data about how easy an attack can occur when website operators let their guard down. For example, of the 65,477 cleanup requests GoDaddy received over the last year, half involved outdated software on the most commonly used platform and tools. In most instances, the biggest vulnerability Content Management Systems (CMS’) faced had to do with its extensibility, specifically the plugins, modules, and extensions website owners deployed and their lack of maintenance.
Once infected, the hackers attack multiple parts and files of a website. On average, the GoDaddy Security Team cleaned up 110 compromised files per hack, and in some cases, it was as many as 35,057 compromised files.
It is not enough to cleanup compromised files. Once infiltrated, hackers regularly create backdoors so they can secretly reenter a platform even after a file cleanup. Of the cleanup requests by GoDaddy customers, in 83 percent of the cases, hackers had created a backdoor. Backdoors are payloads that allow the attacker to bypass existing defensive and access controls, it gives the attacker direct access the environment post-compromise.
Each search engine or security company has its own criteria for blacklisting a website. To get off the blacklist, a small business will likely spend money on security experts or tools to cleanup the infected websites.
Cybersecurity is not about preventing a risk. It is about reducing the risk. It is understandable that small businesses are stretched in so many directions that it is hard to make website security a priority. But even getting started with a few modest steps can help to make an impact.
Here are three tips to help reduce the attack vector, and work load, on your business when thinking about your websites security:
- – Employ strong username/ password combinations, and leverage random password generators and managers where possible. Complex. Long. Unique.
- – Leverage a Website Application Firewall (WAF) to help mitigate attacks that look to leverage vulnerabilities in CMS plugins, extensions, modules and core.
- – Always deploy a strong backup strategy from the beginning, backups are your safety net when all else goes wrong. It should be the first thing you leverage when you go live.
It is as simple as burglar strolling through a mall parking lot with two choices. One car is locked and one isn’t. The choice is obvious.