Kaspersky held their 4th annual Asia Pacific (APAC) Cyber Security Weekend in Siam Reap, Cambodia.
The 4 days conference started on the 18th of September with a theme “Balkanisation: Security Should Not Be in Isolation”. Balkanisation as explained by Managing Director Stephan Neumeier is the fragmentation and isolation of countries.
The event included talks from the Global Research and Analysis Team (GReAT) with Vitaly Kamluk, Director of GReAT APAC starting off with his topic “A Glimpse Into The Future of Internet Through The Eyes of Security Researcher”. Kamluk shared his perspective on the evolution of the Internet stating that the Internet is a collection of “Individual Consciousness” whereby knowledge and information is made accessible to everyone. The collectivity and accessibility are what makes the humans race superior.

Kamluk talked about the dilemma of the Internet – stating that the “Internet full of threats” along with the “Internet must be open” and “Innovations cannot be stopped”. Finding a balance between the 3 factors is difficult and up till now, the UN Group of Government Experts which focuses on Cyber Security, Cyber Conflict and Critical Infrastructure have not come into consensus. Even though private sectors like Microsoft have put up a proposal, they lack the authority to implement their proposal.
Balkinisation may seem like a possible solution to this cyber warfare but Kamluk warns saying that “a divided world is easier to conquer. We need cooperation, collaboration, and mutual trust to effectively thwart these cybercriminals who do acknowledge neither geopolitics nor borders”.
Suguru Ishimaru, a member of the GReAT team shared on his research on the “Roaming Mantis”. This attack leverages vulnerable routers and compromises their dynamic name service (DNS) settings to redirect a link to a rogue server. A DNS service is required for the translation of domain name to IP addresses which is what the computer understands. The rogue server will then return a landing page which may be empty and looks harmless. However, the page may execute codes in the background which may activate a cryptocurrency miner using the processing power of a device causing huge battery drain. The “Roaming Mantis” is also a phishing attack with 27 languages – Arabic, Bulgarian, Czech, Indonesian, Japanese, Korean, Thai, Tagalog, Vietnamese, Traditional Chinese, Simplified Chinese and others. Based on the device language preference, the attack will switch to the default language accordingly. As this is a DNS attack, the link on the navigation bar makes the attack even more convincing.
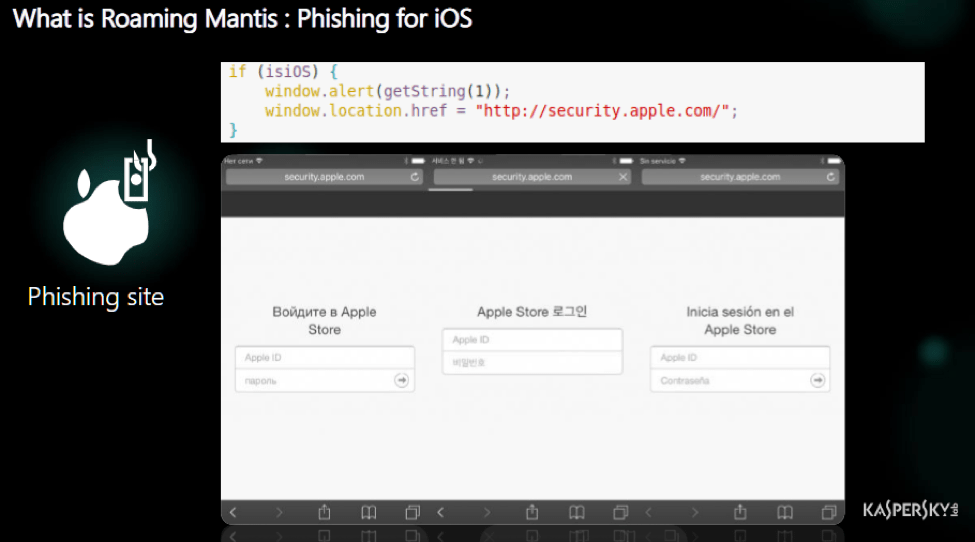
To prevent such attacks, the default login of the router should be change. Staying up to date with the latest patches will also prevent any exploits from this attack. It is not advised to install any applications from untrusted sources downloaded over the internet as the integrity of the application is not verified.
The “Roaming Mantis” is very active and the attackers are rapidly improving through try and errors.
The event continued with Seongsu Park, the GReAT team’s senior security researcher sharing his research and analysis on the topic “Recent (FAKE) Supply Chain Attack of Lazarus”. Lazarus is a notorious advance persistent threat (APT) group. Over the past years, they had made headlines with attacks like the recent Wannacry, Sony’s breach and other cryptocurrency attacks. From the past attacks, the group seems to be state-sponsored with the aim to gain financial profit along with cyber-espionage and sabotage.
Park also shared a high-level view of the Supply Chain attack of Lazarus. As the name suggest, the network of an organization can be seen as a supply chain network – whereby there are different systems performing different activities. A “Supply Chain attack” generally starts off with an APT where information of the network infrastructure is extracted through the malwares. An orchestrated attack will then be performed on the weakest member in the supply network.
The attack was made possible through spearphishing using highly crafted document prepared by Lazarus. The document crafted were extremely convincing in terms of the language used which are almost identical to the original.
The attack also uses landing sites with similar domain name to trick users into believing they are visiting a legitimate website. An example given was the website which has been since taken down, cardanofoundation.org. The attacker purchased the domain cardarnofoundation.org and setup a clone of the legitimate website.
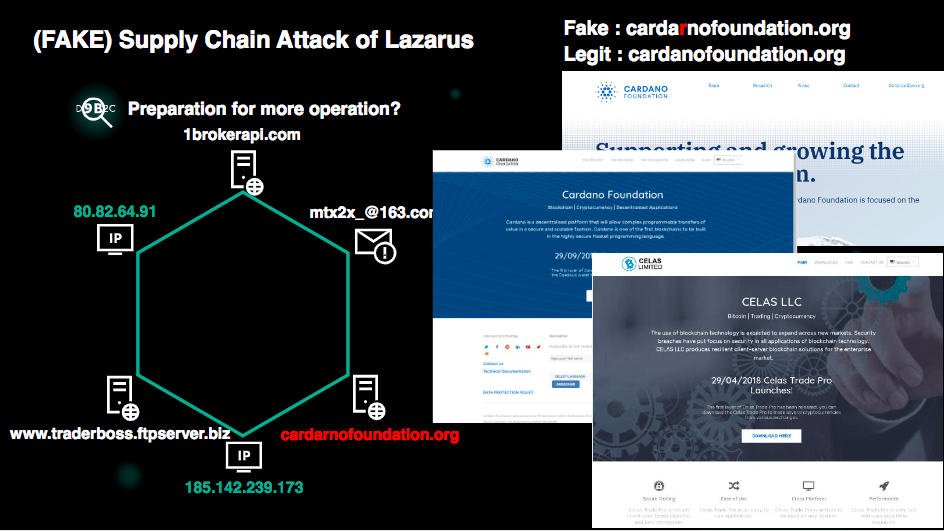
Together with the domain name and SSL which provides the lock icon on most browsers, it reduces the user’s suspicion of the website. This makes the attacker’s website very convincing.
If an unsuspecting user downloads and installs the software, the attackers will have access to the user’s system. Through sophisticated and clever attacks, Lazarus manages to evade anti-virus detection time and time again. The way Kaspersky stays ahead of the attackers is through logs they collected. By analyzing the logs and malware, they are able to determine the entry point of the attack and create rules to detect the malware upon further attacks. It is a cat and mouse game whereby both Kaspersky and cybercriminals evolves on their attack and defenses.
With the recent geopolitical turbulence and internal US political situation, Kaspersky has been under accusations of possibly having a backdoor and unlawful data access by secret services – even though there were no concrete proof.
Anton Shingarev, Vice President of Public Affairs of Kaspersky Lab said that Kaspersky has nothing to hide in the conference. To combat the false accusations, they had come up a multilayered approach.
The multilayered approach includes relocating their data storage and processing to transparency centers located in Switzerland. The next approach is to allow third-party organization to review of independent code and updates. Symantec and McAfee, both competitors of Kaspersky Lab were invited for the reviews but declined to do so. External audit and certification are also obtained for engineering practices. Finally, a redesign of R&D infrastructure and a bug bounty is also introduced to combat the accusations.
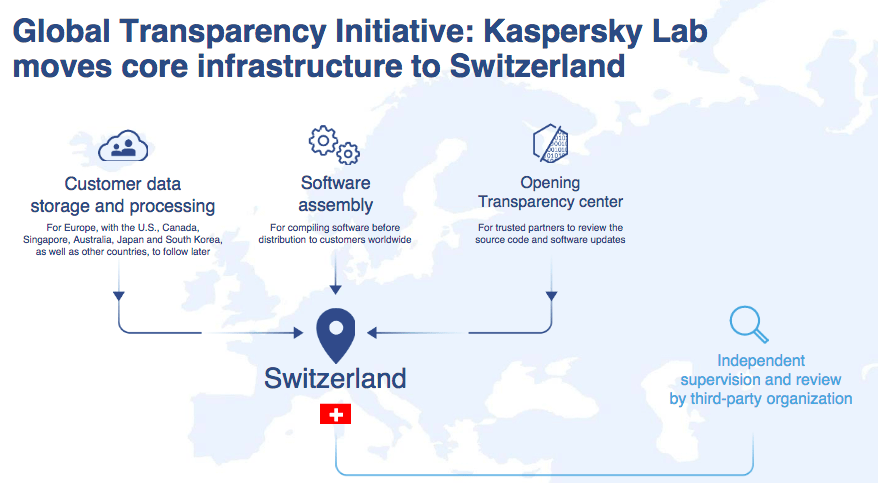
“We take this very seriously, and we are changing. We take this as an opportunity to evolve and become the industrial trendsetter in business practices.” said Anton in the conference. With the goal to detect and protect at all cost, Kaspersky Lab is taking the first step in this changing world.






