With the memory of
the recent WannaCry and Adylkuzz cyberattacks fresh in the minds of
organisations all over the world, it is time for cyber defenders to place more
importance on improving the time it takes to detect breaches and malicious
attacks. In multiple areas of cyber
security, time is currently working in favour of the attackers, and time
is the strategic advantage that the defenders need to regain. The McAfee
commissioned report by Aberdeen titled, “Cyber Security: For Defenders, It’s
About Time”, analyses confirmed breaches and the total time from attacker
compromise to defender detection, also known as attacker dweller time. Key
report findings include:
the recent WannaCry and Adylkuzz cyberattacks fresh in the minds of
organisations all over the world, it is time for cyber defenders to place more
importance on improving the time it takes to detect breaches and malicious
attacks. In multiple areas of cyber
security, time is currently working in favour of the attackers, and time
is the strategic advantage that the defenders need to regain. The McAfee
commissioned report by Aberdeen titled, “Cyber Security: For Defenders, It’s
About Time”, analyses confirmed breaches and the total time from attacker
compromise to defender detection, also known as attacker dweller time. Key
report findings include:
· In cyber security, the
disadvantage of the defenders is highlighted by the distribution of time from
attacker compromise to defender detection: a median of about 38 days, with a
“long tail” of up to four years
disadvantage of the defenders is highlighted by the distribution of time from
attacker compromise to defender detection: a median of about 38 days, with a
“long tail” of up to four years
· For attacks on the
confidentiality of enterprise data, Aberdeen’s analysis shows that twice as
fast at detection and response translates to about 30% less business impact.
confidentiality of enterprise data, Aberdeen’s analysis shows that twice as
fast at detection and response translates to about 30% less business impact.
· For attacks on the
availability of enterprise resources, Aberdeen’s analysis shows that twice as
fast at detection and response translates to about 70% less business
impact.
availability of enterprise resources, Aberdeen’s analysis shows that twice as
fast at detection and response translates to about 70% less business
impact.
· About 80% of the exploits
for a given vulnerability are already in existence by the time it is publicly
disclosed (“zero day”), but just 70% of the vendor-provided patches, fixes, or
workarounds are available — and it may be months before enterprise systems are
actually updated.
for a given vulnerability are already in existence by the time it is publicly
disclosed (“zero day”), but just 70% of the vendor-provided patches, fixes, or
workarounds are available — and it may be months before enterprise systems are
actually updated.
To help organisations better understand the importance
of recapturing the advantage of time from hackers and how they can achieve
this, Aberdeen has provided four illustrative
examples showing how recapturing an advantage of time can help defenders reduce
risk.
of recapturing the advantage of time from hackers and how they can achieve
this, Aberdeen has provided four illustrative
examples showing how recapturing an advantage of time can help defenders reduce
risk.
1.
Time and Data Protection. With the business impact of a data breach
is greatest at the beginning of the exploit, responding twice as fast to data
breaches can lower the business impact by about 30%.
Time and Data Protection. With the business impact of a data breach
is greatest at the beginning of the exploit, responding twice as fast to data
breaches can lower the business impact by about 30%.
2.
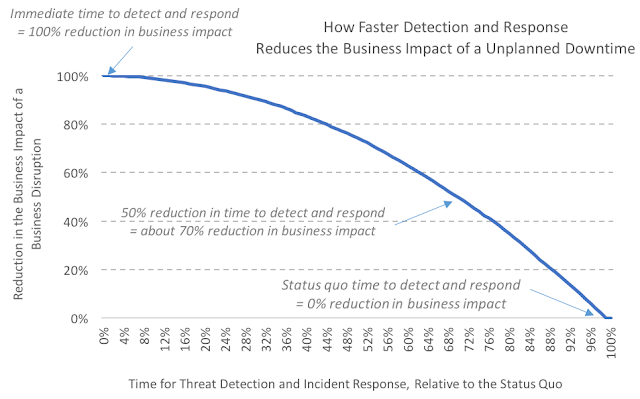
Time and Threat Detection/Incident Response. Apart from data loss,
sophisticated cyberattacks can also result in substantial business impact
involving both the availability and performance of enterprise systems. Being
twice as fast at threat detection and incident response lowers the business
impact of such an attack by about 70%.
Time and Threat Detection/Incident Response. Apart from data loss,
sophisticated cyberattacks can also result in substantial business impact
involving both the availability and performance of enterprise systems. Being
twice as fast at threat detection and incident response lowers the business
impact of such an attack by about 70%.
3.
Time and Data Center/Cloud Security – Traditional vendor
patching is disruptive towards revenue and user productivity. However, with the
speed, reliability and efficiency that virtual patching offers, results in
minimising the two biggest contributors to the total annual business impact of
patching: lost revenue and lost user productivity.
Time and Data Center/Cloud Security – Traditional vendor
patching is disruptive towards revenue and user productivity. However, with the
speed, reliability and efficiency that virtual patching offers, results in
minimising the two biggest contributors to the total annual business impact of
patching: lost revenue and lost user productivity.
4.
Time and Endpoint Security – Endpoint security systems are often
vulnerable to a large volume of vulnerabilities, exploits and the increasing
sophistication of cyberattacks. The way to address these challenges is to not
only provide faster identification and containment of zero-day malware, but
also have flexible approaches in place to sustain the productivity of users and
improve the productivity of responders.
Time and Endpoint Security – Endpoint security systems are often
vulnerable to a large volume of vulnerabilities, exploits and the increasing
sophistication of cyberattacks. The way to address these challenges is to not
only provide faster identification and containment of zero-day malware, but
also have flexible approaches in place to sustain the productivity of users and
improve the productivity of responders.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!