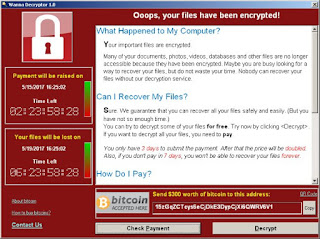
The WannaCry
ransomware was discovered on Friday, and over the weekend has been
detected in over 100 countries. In Singapore, several malls have received this
ransomware message on Sunday morning. Symantec has published a
blogpost which gives insights into what this particular strain of ransomware
is, what it does and how users can protect themselves. You can read the full
post here.
ransomware was discovered on Friday, and over the weekend has been
detected in over 100 countries. In Singapore, several malls have received this
ransomware message on Sunday morning. Symantec has published a
blogpost which gives insights into what this particular strain of ransomware
is, what it does and how users can protect themselves. You can read the full
post here.
What is the situation?
- On
12 May, 2017 a new variant of the Ransom.CryptXXX family
(Detected as Ransom.Wannacry) of
ransomware began spreading widely impacting a large number of
organizations, particularly in Europe. It has now been detected in over
100 countries including Singapore. - WannaCry
encrypts data files and ask users to pay a US$300 ransom in bitcoins. The
ransom note indicates that the payment amount will be doubled after three
days. If payment is not made after seven days, the encrypted files will be
deleted. - WannaCry
has the ability to spread itself within corporate networks, without user
interaction, by exploiting a known vulnerability in Microsoft Windows.
In addition, Nick
Savvides, Security Advocate, Symantec Asia Pacific and Japan has the
following advice for users.
Savvides, Security Advocate, Symantec Asia Pacific and Japan has the
following advice for users.
What to do if you
receive the WannaCry ransomware message? – Please attribute to Nick Savvides,
Security Advocate, Symantec Asia Pacific and Japan
receive the WannaCry ransomware message? – Please attribute to Nick Savvides,
Security Advocate, Symantec Asia Pacific and Japan
- Once the encryption process
starts, there is little the user can do, as it happens very quickly. It is unlikely that the user will notice the
ransomware is encrypting until it’s too late. If the user realizes in the
seconds after running the malware, they may attempt to power off the
machine, then use an external boot disk to boot the machine and run a
cleaner tool like Norton Power Eraser. This may prevent the ransomware
from encrypting all the files. - Any computer that has been
infected should not be trusted. Tools
like Norton Power Eraser, or Norton Internet Security may be able to
remove the infection but the files will still be encrypted. It is always
best to restore the computer either from a backup, or reset to factory
using a recovery disk and then immediately update and apply all patches. - These are important steps, as
we have seen ransomware, that not just ransoms the users’ files, but also
installs banking Trojans to clean out the users’ bank accounts, typically
capturing the users’ banking details when they log into their bank to pay
the ransom. If the back-ups were not encrypted by the ransomware, it is
unlikely that the files were infected. - Symantec recommends affected
users not to pay the ransom. Paying
criminals is never recommended, as it feeds them and rewards them for
their crimes. There is also no guarantee that your files will be released
back to you.
Ransomware stats from
the Symantec Internet Security Threat Report, Volume 22
the Symantec Internet Security Threat Report, Volume 22
- The average ransom per victim
grew to $1,077 in 2016,
up from $294 in 2015 (266% increase). - Ransomware attacks grew
to 463,841 in 2016, up from
340,665 attacks in 2015 (36% increase). - More than 70 percent of malware
attacks on the healthcare industry were ransomware in 2016, including hospitals, pharmacies and insurance
agencies. - 1 in 131 emails contained a malicious link
or attachment in 2016 – the highest rate in five years. - There was a two-fold increase in attempted
attacks against IoT devices over the course of 2016 and, at
times of peak activity, the average device was attacked once every
two minutes.
Ransomware in Singapore in 2016
- Regional rank: 8 (same
as 2015) - Global rank: 24 (up from 42
in 2015) - Percentage of global detections: 0.5%
ransomware infections on unique machines (up from 0.04% in 2015)
Best practices for
protecting against ransomware
protecting against ransomware
- Always keep your
security software up to date to protect yourself against them. - Keep your operating system and
other software updated. Software
updates will frequently include patches for newly discovered security
vulnerabilities that could be exploited by ransomware attackers. - Email is one of the main
infection methods. Be wary of unexpected emails especially
if they contain links and/or attachments. - Be extremely wary of any
Microsoft Office email attachment that advises you to enable macros to
view its content. Unless you
are absolutely sure that this is a genuine email from a trusted source, do
not enable macros and instead immediately delete the email. - Backing up important data is
the single most effective way of combating ransomware infection. Attackers have leverage over their victims by
encrypting valuable files and leaving them inaccessible. If the victim has
backup copies, they can restore their files once the infection has been
cleaned up. However organizations should ensure that back-ups are
appropriately protected or stored off-line so that attackers can’t delete
them. - Using cloud services could help
mitigate ransomware infection, since many retain previous versions of
files, allowing you to “roll back” to the unencrypted form.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!