Late last year, the world felt the stinging blow of the Mirai DDoS attacks, one of the most well-coordinated cyberthreats that was also the largest of its kind in history. Affecting high-profile businesses such as Spotify, Twitter and SoundCloud, the amount of financial and reputational damage this left behind for businesses was monumental.
And it didn’t stop there. Although preventing such attacks could have been as easy as reciting security ABCs, cybercriminals continue to find new loopholes, new sources and new targets to launch malicious attacks. As such, within a span of five months, we have witnessed attacks of the highest sophistication – from BrickerBot to Persirai, from CloudBleed to WannaCry. The reality today is that IoT devices and emerging technologies are a new playground for folks with malicious intent; and according to F5 Network’s latest report, that is not going to change. IoT attacks are not showing any signs of slowing and the industry needs to be anticipating the next Mirai.
With deeper insights into this new reality, F5 Networks has launched its latest Threat Analysis Report: The Hunt for IoT, which takes an investigative look into what the world can expect post-Mirai. The report exposes the networks behind the hunt for IoT devices, the companies that own those networks, and the countries that have been squared as key targets for attackers.
Some of the key insights:
· IoT attacks grew 1,373% from Q1 through Q4 last year (up 110% from Q3 to Q4) and patterns suggest that the same threat actors were consistently participating in the hunt.
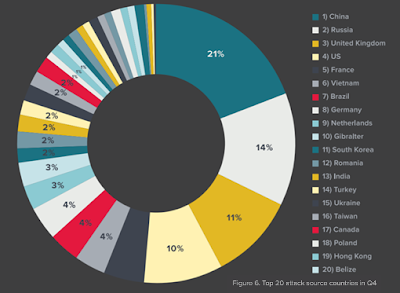
· Networks in China remained at the top of the threat actor list in Q3 & Q4
o Primarily state-owned Chinese telecom companies and ISPs headlined the threat actor list, accounting for 44% of all attacks in Q3 and 21% in Q4. Trailing behind China, the top threat actors in Q3 were Vietnam and the US, and Russia and the UK in Q4.
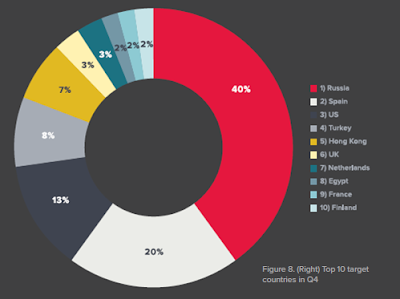
· Top 4 targeted countries in Q3 & Q4 were consistent
o Russia, Spain, US, Turkey. Russia in particular jumped from 31% to 40% of total attack volume received between Q3 and Q4, coinciding with the US election.
What does this mean for enterprises and what should they do to deal with the IoT threat?
- Have a DDoS strategy that can support attack sizes beyond your network capacity.
- Put pressure on IoT manufacturers to secure their products, and do not buy products that are known to be insecure or compromised.
- Share your knowledge—about vulnerable devices, attacks and threat actors, successful mitigation efforts, and potential solutions—with other security professionals.
Threat Analysis Report: The Hunt for IoT is the second volume of F5 Lab’s IoT reports, following the first volume DDoS’s Newest Minions: IoT Devices. To find out more on the subject, the full report is available here with further detail on global and market trends.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!