Companies
now outnumbers distrust for public clouds by more than 2-to-1.
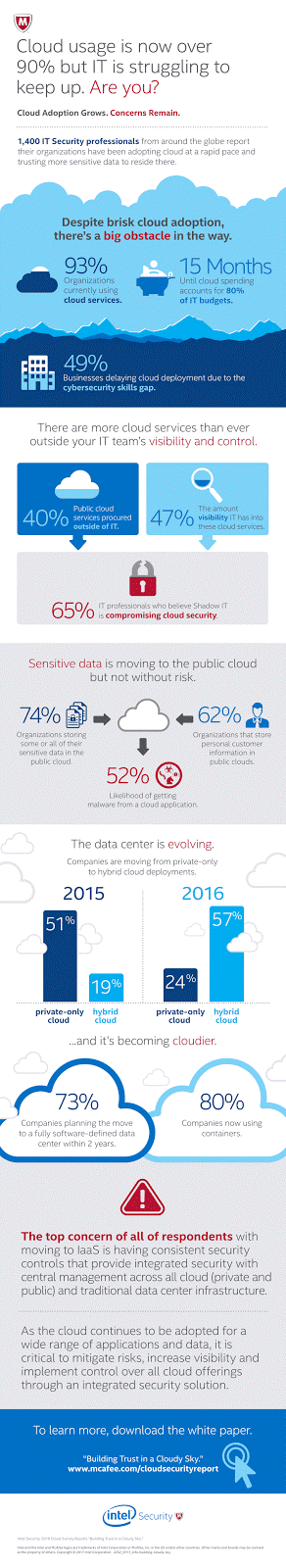
percent of professionals slowed cloud adoption due to a lack of cybersecurity
skills.
percent think Shadow IT is interfering with keeping the cloud safe and secure.
percent indicate a malware infection can be tracked to a cloud application.
percent store sensitive customer information in the public cloud.
security report, “Building Trust in a Cloudy Sky.” The report outlines the
current state of cloud adoption, the primary concerns with private and public
cloud services, security implications, and the evolving impact of Shadow IT of
the more than 2,000 IT professionals surveyed.
Many organizations in Southeast Asia have incorporated a ‘Cloud First’ strategy
into their architectures,” said David Allott, Director of Cyber Defense, APAC,
Intel Security. “Those who have yet to do so, are rapidly striving towards
cloud adoption. We saw that in 2016, 57 percent of organizations shifted to
hybrid cloud models, compared to just 24 percent in 2015. This is an indication
of the ever growing state of cloud adoption among organizations.”
Trust in the Cloud on the Rise
The trust and perception of public cloud services continues to improve year
over year. Most organizations view cloud services as or more secure than
private clouds, and more likely to deliver lower costs of ownership and overall
data visibility. Those who trust public clouds now outnumber those who distrust
public clouds by more than 2-to-1. Improved trust and perception, as well as
increased understanding of the risks by senior management, is encouraging more
organizations to store sensitive data in the public cloud. Personal customer
information is the most likely type of data to be stored in public clouds, kept
there by 62 percent of those surveyed.
Risks Also Rise: Shadow IT and the Cybersecurity Skill Shortage
The ongoing shortage of security skills is continuing to affect cloud
deployments. Almost half of the organizations surveyed report the lack of
cybersecurity skills has slowed adoption or usage of cloud services, possibly
contributing to the increase in Shadow IT activities. Another 36 percent report
they are experiencing a scarcity but are continuing with their cloud activities
regardless. Only 15 percent of those surveyed state they do not have a skills
shortage.
Due to the ease of procurement, almost 40 percent of cloud services are now
commissioned without the involvement of IT, and unfortunately, visibility of
these Shadow IT services has dropped from about 50 percent last year to just
under 47 percent this year. As a result, 65 percent of IT professionals think
this phenomenon is interfering with their ability to keep the cloud safe and
secure. This is not surprising given the amount of sensitive data now being
stored in the public cloud and more than half (52 percent) of respondents
reporting they have definitively tracked malware from a cloud SaaS application.
Data Center Progression
The number of organizations using private cloud only has dropped from 51
percent to 24 percent over the past year, while hybrid cloud use has increased
from 19 percent to 57 percent. This move to a hybrid private/public cloud
architecture requires the data center to evolve to a highly virtualized,
cloud-based infrastructure. On average, 52 percent of an organization’s data
center servers are virtualized, 80 percent are using containers and most expect
to have the conversion to a fully software-defined data center completed within two years.
Recommendations:
will look for the easiest targets, regardless of whether they are public,
private or hybrid. Integrated or unified security solutions that provide
visibility across all of the organization’s services could be the best defense.
credentials, especially for administrators, will be the most likely form of
attack. Organizations need to ensure they are using authentication best
practices, such as distinct passwords, multi-factor authentication and even
biometrics where available.
technologies such as data loss prevention, encryption and cloud access security
brokers (CASBs) remain underutilized. Integrating these tools with an existing
security system increases visibility, enables discovery of shadow services, and
provides options for automatic protection of sensitive data at rest and in
motion throughout any type of environment.
need to evolve toward a risk management and mitigation approach to information
security. They should consider adopting a Cloud First strategy to encourage
adoption of cloud services to reduce costs and increase flexibility, and put
security operations in a proactive position instead of a reactive one.
download the full report, visit www.mcafee.com/cloudsecurityreport.
In fall 2016, Intel Security surveyed over 2,000 IT professionals across a
broad set of industries, countries and organization sizes. Research
participants were senior technical decision-makers from small, medium and large
organizations located in Australia, Brazil, Canada, France, Germany, Japan,
Mexico, Saudi Arabia, Singapore, the United Arab Emirates, the United Kingdom
and the United States
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!