Surge of email attacks using malicious WSF attachments
Over the
past three months, Symantec has seen a major increase in the number of
email-based attacks using malicious Windows Script File (WSF) attachments.
Ransomware attack groups in particular have been employing this new tactic.
past three months, Symantec has seen a major increase in the number of
email-based attacks using malicious Windows Script File (WSF) attachments.
Ransomware attack groups in particular have been employing this new tactic.
WSF files are designed to allow a
mix of scripting languages within a single file. They are opened and run by the
Windows Script Host (WSH). Files with the .wsf extension are not automatically
blocked by some email clients and can be launched like an executable file.
mix of scripting languages within a single file. They are opened and run by the
Windows Script Host (WSH). Files with the .wsf extension are not automatically
blocked by some email clients and can be launched like an executable file.
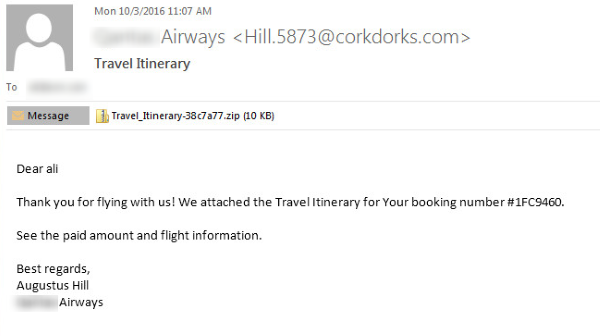
Malicious WSF files have been
used in a number of recent major spam campaigns spreading Locky. For example,
between October 3 and 4, Symantec blocked more than 1.3 million emails bearing
the subject line “Travel Itinerary.” The emails purported to come
from a major airline and came with an attachment that consisted of a WSF file
within a .zip archive. If the WSF file was allowed to run, Locky was installed
on the victim’s computer.
used in a number of recent major spam campaigns spreading Locky. For example,
between October 3 and 4, Symantec blocked more than 1.3 million emails bearing
the subject line “Travel Itinerary.” The emails purported to come
from a major airline and came with an attachment that consisted of a WSF file
within a .zip archive. If the WSF file was allowed to run, Locky was installed
on the victim’s computer.
Figure 1. Example of recent Locky campaign using malicious WSF
files within .zip attachments
files within .zip attachments
These recent Locky campaigns are
part of a broader trend. Over the past number of months, Symantec has noticed a
significant increase in the overall numbers of emails being blocked containing
malicious WSF attachments. From just over 22,000 in June, the figure shot up to
more than 2 million in July. September was a record month, with more than 2.2
million emails blocked.
part of a broader trend. Over the past number of months, Symantec has noticed a
significant increase in the overall numbers of emails being blocked containing
malicious WSF attachments. From just over 22,000 in June, the figure shot up to
more than 2 million in July. September was a record month, with more than 2.2
million emails blocked.
Groups who spread malware through
spam campaigns frequently change the format of the malicious attachments used.
As security vendors improve their defenses against certain malicious file
types, attack groups will switch to alternatives in the hope that more emails
will slip through defenses.
spam campaigns frequently change the format of the malicious attachments used.
As security vendors improve their defenses against certain malicious file
types, attack groups will switch to alternatives in the hope that more emails
will slip through defenses.
In a constantly shifting threat
landscape, organizations need to remain vigilant and aware that threats can
come from new and unanticipated sources.
landscape, organizations need to remain vigilant and aware that threats can
come from new and unanticipated sources.
Tips on protecting yourself from
- Regularly back up any
files stored on your computer. If your computer does become infected with
ransomware, your files can be restored once the malware has been - Always keep your security
software up to date to protect yourself against any new variants of - Keep your operating system
and other software updated. Software updates will frequently include patches
for newly discovered security vulnerabilities that could be exploited by - Delete any
suspicious-looking emails you receive, especially if they contain links or - Be extremely wary of any
Microsoft Office email attachment that advises you to enable macros to view its
content. Unless you are absolutely sure that this is a genuine email from a
trusted source, do not enable macros and instead immediately delete the email.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!