Detection of the Locky Ransomware with Hillstone iNGFW
Hillstone Networks Intelligent Next Generation Firewall provide an effective way to detect Locky ransomware which has been quickly spreading worldwide
Hillstone Networks iNGFW has effectively detected the Locky ransomware and its variants, ensuring businesses do not fall victim to Locky’s malicious intent.
The Characteristics of Locky Ransomware
Locky is a ransomware that is usually contained within a Microsoft Word document sent by email as an attachment – often as an invoice – to large numbers of recipients using a massive spam campaign. Since its first appearance, Locky has spread rapidly and infected thousands of computers hourly, according to research.
Once the attachment is opened, the ransomware is installed and enabled on the victim’s computer. It tries to download Portable Executable (PE) files from a remote control server and executes it from there. It then encrypts every file in the local drive, as well as the network, using RSA-2048 and AES-1024 algorithms.
It subsequently displays messages on the victim’s machine and tells the victim to visit an attacker’s website for further instructions and ransom payment in order to decrypt the previously encrypted files. The ransom demand varies and can be paid using bitcoin.
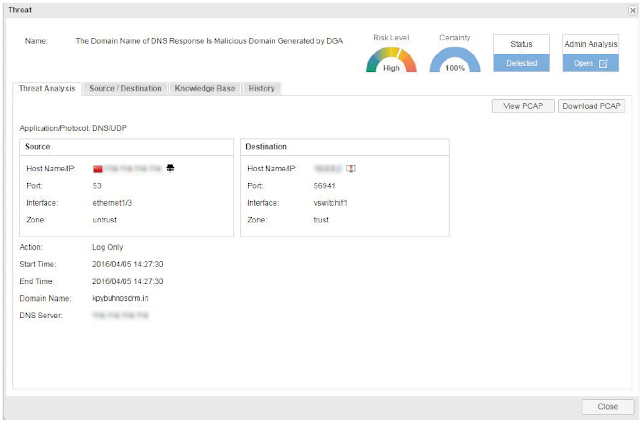
Detecting Locky Ransomware with Hillstone iNGFW
The detection and protection mechanisms on Hillstone Networks iNGFW include the following:
- Anti-Virus engines include latest signatures that can be used to pattern-match the Locky email spams, which contain malicious attachments or download files.
- Reputation engine consists of an IP and domain name reputation database that includes the list of known, relevant malicious IP and domain names.
- Domain Generation Algorithms (DGA) detection engine can be used to detect DGA domain names that are used as the C&C server
- Threat intelligence correlation module can correlate different threat events andalerts, as well as draw more accurate conclusions out of individual threat alerts.
- Cloud intelligent system can perform further threat analysis on suspicious threat events or objects.
For detailed information, read the “Detection of the Locky Ransomware” blog post or download a complimentary copy at http://www.hillstonenet.com/register.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!