Singapore among Asian countries with lowest
malware encounter rates, despite high concentration of malware hosting sites –
Microsoft Report
malware encounter rates, despite high concentration of malware hosting sites –
Microsoft Report
The latest Microsoft Security Intelligence
Report, Volume 22, revealed that emerging countries in Asia still among the
most vulnerable to malware attacks in the first quarter of 2017
Report, Volume 22, revealed that emerging countries in Asia still among the
most vulnerable to malware attacks in the first quarter of 2017
SINGAPORE, 5 September 2017 – Microsoft released findings from the
global Security
Intelligence Report (SIR), Volume 22, which placed Singapore among the Asian countries with the
lowest malware encounter rates for the period of January to March 2017. The
report also found that Singapore has a high concentration of malware hosting
sites during the same period, with 21.6 malware-hosting sites for every 1,000
websites screened by Microsoft real-time security products.
global Security
Intelligence Report (SIR), Volume 22, which placed Singapore among the Asian countries with the
lowest malware encounter rates for the period of January to March 2017. The
report also found that Singapore has a high concentration of malware hosting
sites during the same period, with 21.6 malware-hosting sites for every 1,000
websites screened by Microsoft real-time security products.
Microsoft’s bi-annual Security Intelligence
Report (SIR) provides in-depth data and insights into the global threat
landscape, particularly in software vulnerabilities, exploits, malware and
web-based attacks. In this latest version, the report tracked endpoint[1] and cloud
threat data and profiled more than 100 individual markets. It also shared best practices and solutions that can help
organisations better protect, detect and respond to threats.
Report (SIR) provides in-depth data and insights into the global threat
landscape, particularly in software vulnerabilities, exploits, malware and
web-based attacks. In this latest version, the report tracked endpoint[1] and cloud
threat data and profiled more than 100 individual markets. It also shared best practices and solutions that can help
organisations better protect, detect and respond to threats.
“Technological advancements bring a host of
cyberthreats that have the potential to shake the trust people have in
technology. By sharing security intelligence in a timely manner to provide
visibility for individuals and organisations to understand the cyberthreat
landscape, Microsoft can empower them with the ability to protect, detect and
respond to cyberthreats faster. As Singapore accelerates the building of a
Smart Nation, insights such as these will become increasingly important to our
customers and partners, who will be playing integral roles in making the Smart
Nation vision a reality,” said
Richard Koh, Chief Technology Officer, Microsoft Singapore.
cyberthreats that have the potential to shake the trust people have in
technology. By sharing security intelligence in a timely manner to provide
visibility for individuals and organisations to understand the cyberthreat
landscape, Microsoft can empower them with the ability to protect, detect and
respond to cyberthreats faster. As Singapore accelerates the building of a
Smart Nation, insights such as these will become increasingly important to our
customers and partners, who will be playing integral roles in making the Smart
Nation vision a reality,” said
Richard Koh, Chief Technology Officer, Microsoft Singapore.
Asian countries among the most vulnerable to
malware
malware
The SIR Volume 22 report found that emerging
Asian economies such as Bangladesh, Pakistan and Indonesia have the highest
malware encounter rates in the world. Approximately one in four computers
running Microsoft real-time security products in these countries reported a
malware encounter during January to March 2017.
Asian economies such as Bangladesh, Pakistan and Indonesia have the highest
malware encounter rates in the world. Approximately one in four computers
running Microsoft real-time security products in these countries reported a
malware encounter during January to March 2017.
Singapore registers fourth lowest malware
encounter rate in Asia
encounter rate in Asia
Together with other markets in the region with
higher levels of IT maturity such as Australia, Japan and New Zealand, Singapore
registered malware encounter rates that are lower than the worldwide average.
higher levels of IT maturity such as Australia, Japan and New Zealand, Singapore
registered malware encounter rates that are lower than the worldwide average.
Ranked 18 out of 21 countries, Singapore
registered the fourth lowest malware encounter rates in Asia. Singapore also
made improvements with lower malware encounter rates of between 5.3 percent and
7.9 percent recorded in January to March 2017, versus rates of 20.2 percent
recorded during the same period in 2016.
registered the fourth lowest malware encounter rates in Asia. Singapore also
made improvements with lower malware encounter rates of between 5.3 percent and
7.9 percent recorded in January to March 2017, versus rates of 20.2 percent
recorded during the same period in 2016.
Malware encounter rates for markets in Asia in
Q1 2017 (from highest to
lowest):
Q1 2017 (from highest to
lowest):
|
1.
Bangladesh 2.
Pakistan 3.
Cambodia 4.
Indonesia 5.
Mongolia 6.
Myanmar 7.
Vietnam |
8.
Nepal 9.
Thailand 10.
Philippines 11.
Sri Lanka 12.
China 13.
India 14.
Malaysia |
15.
Taiwan 16.
Korea 17.
Hong Kong 18.
Singapore 19.
Australia 20.
New Zealand 21.
Japan |
Ransomware attacks on the rise
Ransomware is one of the most infamous malware
families in 2017. In the first half of this year, two waves of ransomware
attacks, WannaCrypt and Petya,
exploited vulnerabilities in outdated Windows operating systems worldwide and
disabled thousands of devices by illegitimately restricting access to data
through encryption. This not only disrupted individuals’ daily lives but also
crippled many enterprises’ operations.
families in 2017. In the first half of this year, two waves of ransomware
attacks, WannaCrypt and Petya,
exploited vulnerabilities in outdated Windows operating systems worldwide and
disabled thousands of devices by illegitimately restricting access to data
through encryption. This not only disrupted individuals’ daily lives but also
crippled many enterprises’ operations.
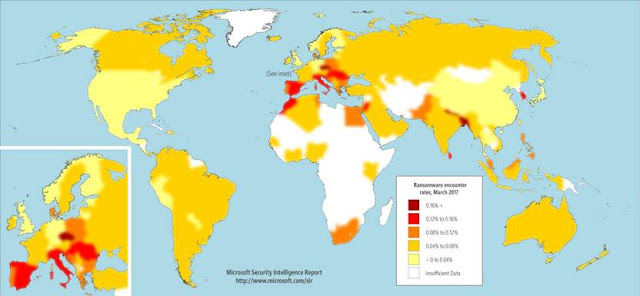
The attacks are disproportionately
concentrated in Europe while most of the Asia markets have not been too heavily
impacted. In fact, Japan and China have been listed as the two top countries
with the lowest ransomware encounter rate. One of the few exceptions in the
region is Korea where it has the second highest ransomware occurrences
worldwide.
concentrated in Europe while most of the Asia markets have not been too heavily
impacted. In fact, Japan and China have been listed as the two top countries
with the lowest ransomware encounter rate. One of the few exceptions in the
region is Korea where it has the second highest ransomware occurrences
worldwide.
Attackers evaluate several factors when
determining what regions to target, such as a country’s GDP, average age of
computer users and available payment methods. The region’s language can also be
a key contributing factor as a successful attack often depends on an attacker’s
ability to personalise a message to convince a user to execute the malicious
file.
determining what regions to target, such as a country’s GDP, average age of
computer users and available payment methods. The region’s language can also be
a key contributing factor as a successful attack often depends on an attacker’s
ability to personalise a message to convince a user to execute the malicious
file.
Global
encounter rates for ransomware families in March 2017
encounter rates for ransomware families in March 2017
Globally, Win32/Spora has rapidly become one of the most widespread ransomware
families and it was the most commonly encountered ransomware family in March
2017. Spora encrypts files with several popular extensions, including .doc,
.docx, .jpg, .pdf, .xls, .xlsx, and .zip. This
ransomware also has worm capability, making it capable of spreading to other
computers in the network.
families and it was the most commonly encountered ransomware family in March
2017. Spora encrypts files with several popular extensions, including .doc,
.docx, .jpg, .pdf, .xls, .xlsx, and .zip. This
ransomware also has worm capability, making it capable of spreading to other
computers in the network.
Cloud accounts and services under cyber siege
As cloud migration increases, the cloud has
become the central data hub for a majority of organisations. This also
translates into more valuable data and digital assets being stored the cloud,
making it a growing target for cybercriminals. SIR Volume 22 highlighted a 300
percent increase in consumer and enterprise accounts managed in the cloud being
attacked globally over the past year while the number of logins attempted from
malicious IP addresses has increased by 44 percent year over year.
become the central data hub for a majority of organisations. This also
translates into more valuable data and digital assets being stored the cloud,
making it a growing target for cybercriminals. SIR Volume 22 highlighted a 300
percent increase in consumer and enterprise accounts managed in the cloud being
attacked globally over the past year while the number of logins attempted from
malicious IP addresses has increased by 44 percent year over year.
In addition, a large majority of these
compromises are the result of weak, guessable passwords and poor password
management, followed by targeted phishing attacks and breaches of third-party
services. As the frequency and sophistication of attacks on user accounts
in the cloud accelerates, there is an increased emphasis on the need to move
beyond passwords for authentication.
compromises are the result of weak, guessable passwords and poor password
management, followed by targeted phishing attacks and breaches of third-party
services. As the frequency and sophistication of attacks on user accounts
in the cloud accelerates, there is an increased emphasis on the need to move
beyond passwords for authentication.
Building trust in the
digital world by strengthening cybersecurity posture
digital world by strengthening cybersecurity posture
As the threat landscape continues to evolve
and grow, organisations need to ensure they have a solid cybersecurity
architecture and robust cyber hygiene best practices. This will enable them to
better protect their digital environment, detect threats and respond to
attacks.
and grow, organisations need to ensure they have a solid cybersecurity
architecture and robust cyber hygiene best practices. This will enable them to
better protect their digital environment, detect threats and respond to
attacks.
Here are four best practices that individuals
and organisations can consider to minimise their cyber risk exposures and stay
resilient in an everchanging threat landscape.
and organisations can consider to minimise their cyber risk exposures and stay
resilient in an everchanging threat landscape.
- Do not work in public Wi-Fi hotspots where attackers could eavesdrop on digital
communications, capture logins and passwords, and access personal data. - Regularly update the operating system and other software programs to ensure
the latest patches are installed. This reduces the risk of vulnerability
exploitation. Users should also install the most recent release of Windows
10 to take advantage of its improved hardening and security mitigations. - Reduce risk of credential compromise by educating users on why they should avoid simple
passwords and enforcing multi-factor authentication methods. For example,
the Azure Multi-Factor Authentication
(MFA) provides organisations
with a two-step verification solution that helps safeguard access to data
and applications while meeting user demand for a simple sign-in process by
delivering strong authentication via a range of easy verification options. - Enforce security policies that control
access to sensitive
data and limit corporate network access to appropriate users, locations,
devices, and operating systems. For example, Microsoft Azure Active Directory Identity Protection enables enterprises to configure
risk-based policies to automatically protect the identities across their
organisation. These policies can automatically block the user without the
proper authorisation or offer suggestions that include password resets and
multi-factor authentication enforcement.
“As technology continues to permeate every
part of our work and personal lives, security cannot be an afterthought. At
Microsoft, our products and services are designed and built with security in
mind. By making a security a priority in all that we do, we can help build
greater trust in technology and pave the way for everyone to harness its
fullest potential,” said Richard Koh, Chief Technology Officer, Microsoft
Singapore.
part of our work and personal lives, security cannot be an afterthought. At
Microsoft, our products and services are designed and built with security in
mind. By making a security a priority in all that we do, we can help build
greater trust in technology and pave the way for everyone to harness its
fullest potential,” said Richard Koh, Chief Technology Officer, Microsoft
Singapore.
To download and learn
more about the Microsoft Security Intelligence Report findings, visit www.microsoft.com/sir and the Microsoft Secure Blog.
more about the Microsoft Security Intelligence Report findings, visit www.microsoft.com/sir and the Microsoft Secure Blog.
For the LATEST tech updates,
FOLLOW us on our Twitter
LIKE us on our FaceBook
SUBSCRIBE to us on our YouTube Channel!